TrustBuilder Windows Logon
TrustBuilder Windows Logon allows a user to open a Windows session using TrustBuilder Authenticator mobile app. The administration of this feature is done from the Admin Console V2, and is managed as a connector in a given service.
TrustBuilder Windows Logon is subject to commercial license. Contact your TrustBuilder partner for more information.
⚠️ Important recommendation → We recommend trying TrustBuilder Windows Logon on a few workstations to make sure it covers all your use cases and your Windows configuration, prior to activating it massively and removing the Windows password credential provider.
Overview
TrustBuilder Windows Logon enables the opening of an interactive session by adding a MFA authentication to the user password.
![]() SUPPORTED
SUPPORTED
The supported use cases are the following:
Opening a session with a local or domain account, while the workstation is online:
with the user’s mobile phone
without the user’s mobile phone, using a “scratch code” provided by the helpdesk (use case: the user forgot his phone)
Opening a session with a local or domain account, while the workstation is offline using a “scratch code” revealed on the user’s mobile phone (use case: no network)
Opening a session with a local or domain account, via Remote desktop connection if RDP is authorized
![]() CURRENTLY NOT SUPPORTED
CURRENTLY NOT SUPPORTED
The currently not supported scenarios are the following:
Credentialed User Access Control (UAC) elevation requests, also known as “Run as administrator”
Opening a session with a Microsoft account. In this case, the MFA authentication is not applied.
See “Current limitations” section
Requirements
TrustBuilder license
The TrustBuilder Windows Logon option has to be activated with a maximum number of workstations defined
(Please contact our sales department if you want this option to be enabled on your service)
TrustBuilder user account
Users should have an ‘ACTIVE’ status: during TrustBuilder Windows Logon sign-in, users cannot enroll themselves (activate a first device). This means that users should have at least one active device to be used for authentication through TrustBuilder MFA. Users without an active device attempting to sign into TrustBuilder Windows Logon will receive an authentication failed response from TrustBuilder.
The TrustBuilder user’s login should match the Windows username (more info)
All users must have a smartphone running TrustBuilder Authenticator.
Windows user account
Users will open a session using the following:
a local account
a domain account
The account must have a password defined.
Microsoft accounts are not supported.
For local accounts, the following security policy settings (Windows10) are not supported: “Interactive logon: don’t display username at sign-in” and “Interactive logon: don’t display last signed-in”.
Workstations
Workstations should be running Windows 10 20H2 or later, or Windows 11.
All workstations should be able to communicate with TrustBuilder on TCP port 443. Note that HTTP proxies are currently not supported.
Installation of Microsoft Visual Studio C++ Redistributable is required (The package is already included in the standard Windows OS installations)
Supported authentication methods
Push notifications to TrustBuilder Authenticator app
The offline mode is supported from TrustBuilder Authenticator version 6.22 and later. For standard mode, all TrustBuilder Authenticator versions are supported.
Recommendations
The TrustBuilder Windows Logon feature protects the session opening. In order to fully protect the workstation, we recommend to protect the data located on the workstation by using a hard drive encryption mechanism.
The offline “Scratch Codes” are located in TrustBuilder Authenticator on the user’s phone. In order to protect these codes we recommend activating the automatic screen lock feature on users’ phones.
For more information about credential providers in Windows and to hide other credential providers, please refer to the Microsoft documentation → Credential Provider in Windows
Installation & Configuration
Here are the basic configuration steps:
Step 3- Install TrustBuilder Windows Logon ⚠ TrustBuilder supports manual installation, silent installation and mass deployment. Before deploying massively, make sure the feature fully matches your use case.
Step 4- Test your setup
Step 5- Perform mass deployment
1. Activate TrustBuilder Windows Logon option
Go to the administration console > Service Parameters tab.
Check that the Windows Logon parameter is set to Yes.
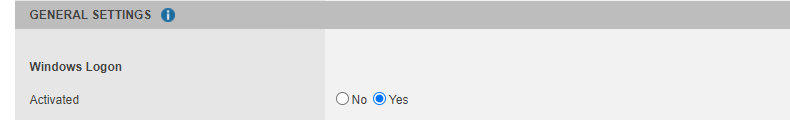
If you do not see the Windows Logon parameter, it means that the option is not activated for your service. Please contact our sales department if you want this option to be enabled on your service.
2. Create and configure the connector
TrustBuilder Windows Logon is managed as a connector from the administration console V2 (know more about administration console v2).
When deleting a connector, make sure to delete all workstations within this connector prior to deleting it.
Log in to the admin console V2.
Go to the “Windows Logon” section.
Click on + Add connector.
Provide a connector name and click on + Add.

Click on Edit to display the connector’s parameters.
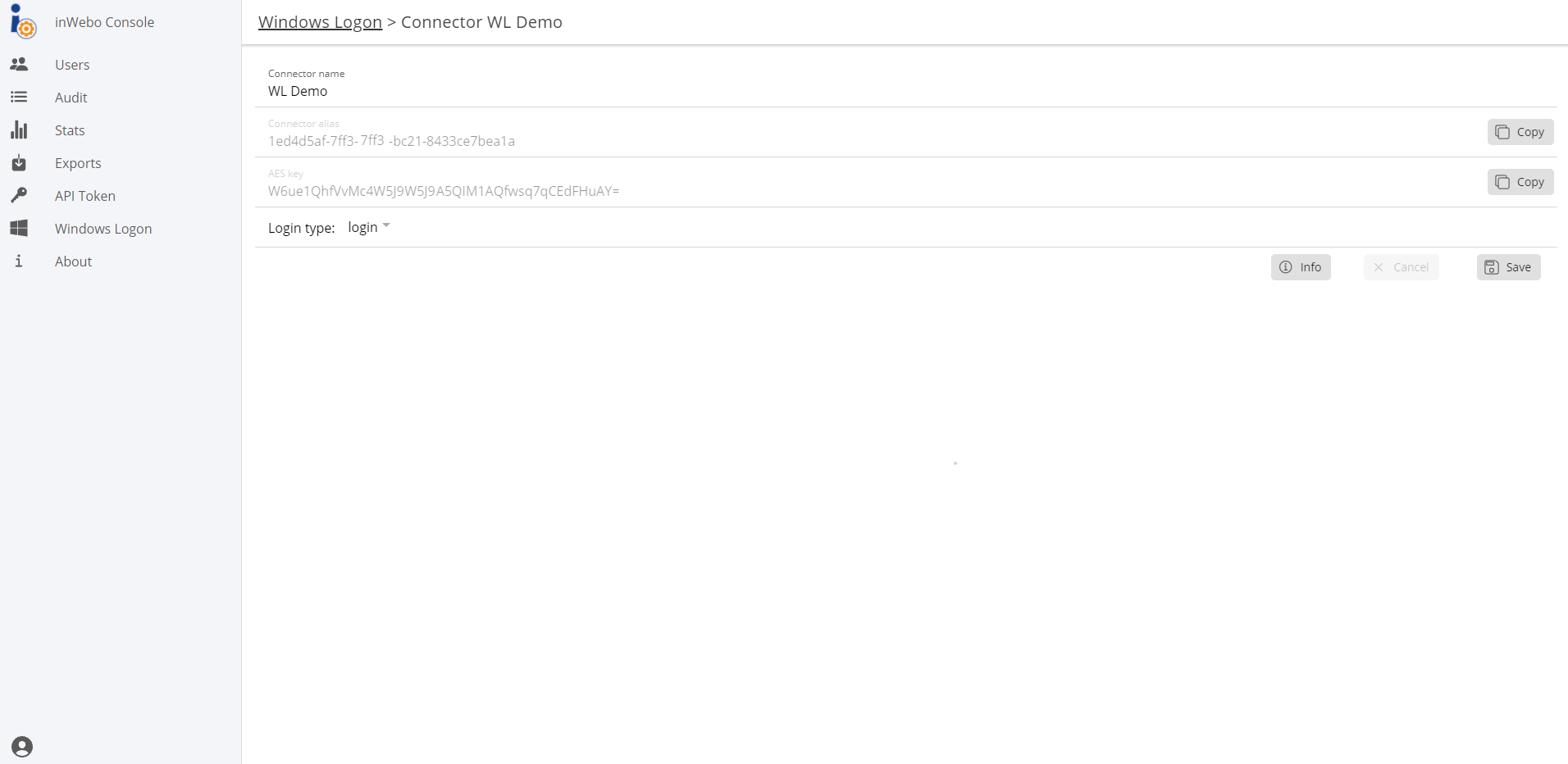
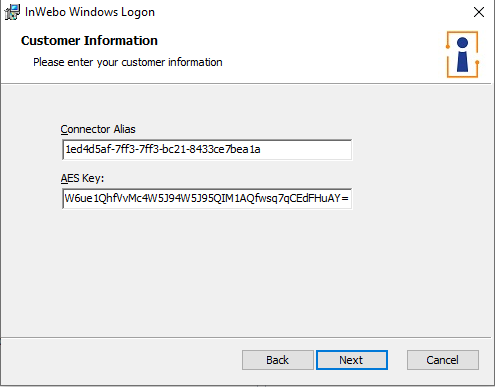
At creation, the connector automatically contains a connector alias and an AES key:
the connector alias identifies the connector,
the AES key is a security item that will be used to activate the feature on a workstation.
About Login type setting
You can select ‘login’ or ‘login2’. The selected login must match the users Windows login.
The default value is ‘Login’.
‘login2’ can be used when the login used for Windows sign-in differs from the TrustBuilder login.
Offline mode parameters
You will soon be able to configure the offline mode parameters. In the meantime, the default values are used.
Number of scratch codes → By default, 20 scratch codes may be generated per user:
15 scratch codes in the user's details from the admin console
5 scratch codes in the user's Authenticator application.
When 3 scratch codes are consumed, and the user performs an online session opening, the user's full set of scratch codes is renewed.
Validity of scratch codes → the validity period of a scratch code is 90 days.
Scratch code renew frequency → the user's full set of scratch codes is renewed every 30 days.
3. Install the TrustBuilder credential provider
The TrustBuilder Windows Logon installer can be downloaded from Resources Downloads page.
To install TrustBuilder Windows Logon on the workstations, TrustBuilder supports manual installation, silent installation and automated deployment. This requires administrator rights.
When the installation is successful, you should see TrustBuilder MFA as an sign-in option in the Windows logon screen.
.png?inst-v=3deda485-6e03-414c-a98c-84a1ab84ee1e)
Version upgrade
To upgrade TrustBuilder Windows Logon, install a higher version. You can download the latest version of TrustBuilder Windows Logon from Resources Downloads page. The configuration information will be retrieved from the appsetting file.
Note that the upgrade is not automated.
A configuration file ‘appsettings.json’ is automatically created by the installer. To access it:
Go to the folder c:\Programs\InWebo\WindowsLogon and open the ‘appsettings.json’ file.
From the appsetting.json file, you can edit the ConnectorAlias and the AES key (run as an administrator).
{
"Logging": {
"LogLevel": {
"Default": "Information",
"Microsoft": "Warning",
"Microsoft.Hosting.Lifetime": "Information"
}
},
"HttpClientConfig": {
"ConnectorAlias": "1td4d5af-e5f4-4518-aie2-88fef8e3827a",
"BaseURI": "https://kiwi.myinwebo.com/auth/v2/anonymous/sesame/"
},
"Aes": "JLlUV0CNNfrf1j9U3khjE/GzLjykk9Buyy8J/e019/=A"
}Manage workstations
From the admin console V2, go to the “Windows Logon” section.
Go to the connector and click on “Workstations”. You will get the activated workstations list for this connector.

Click on the details arrow on the right. You will see the workstation name, its uuid, the user that initiated the workstation, and also creation and validity dates.
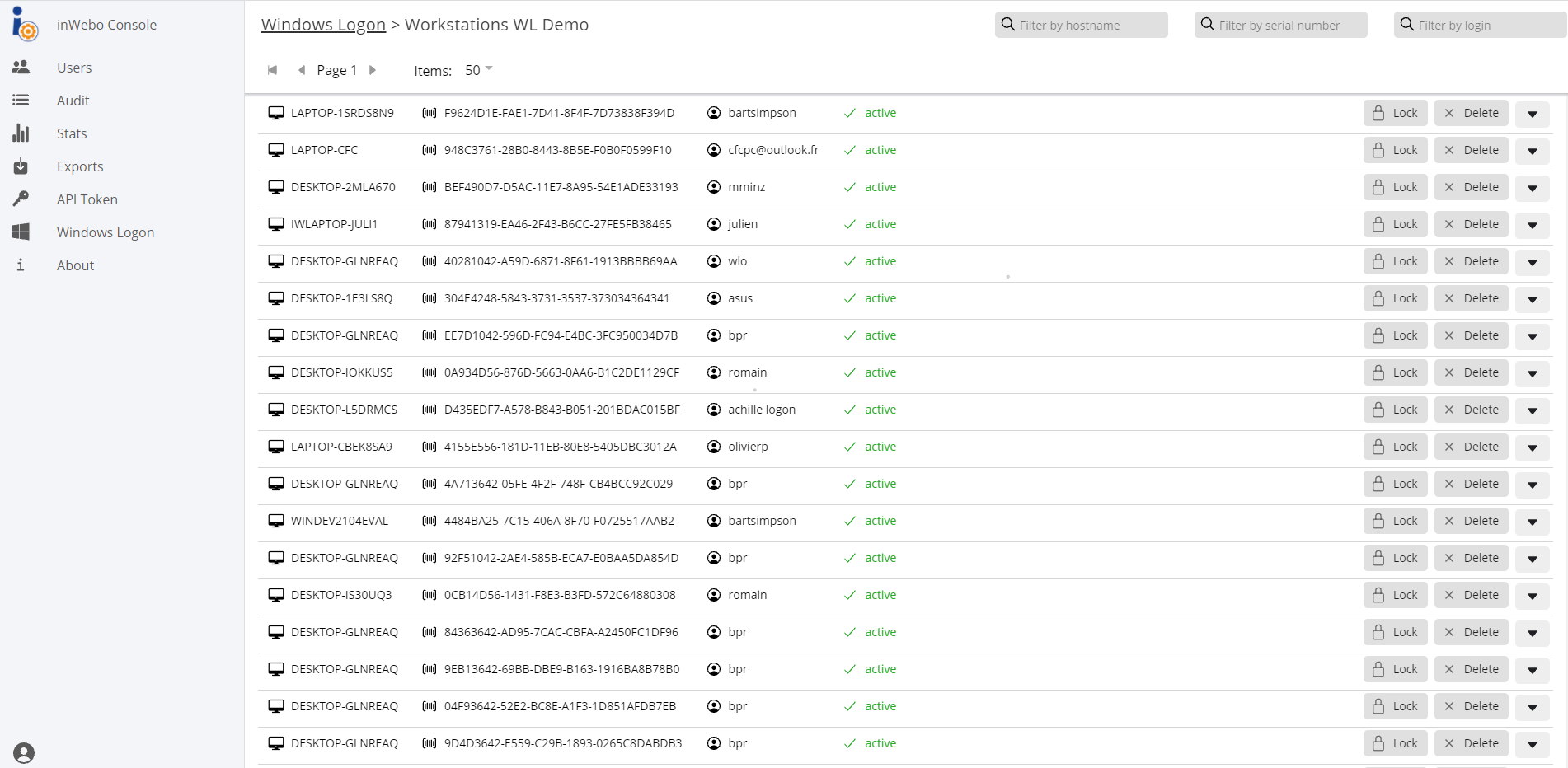
The following actions can be performed:
Locking a workstation → this will prevent users from opening a session on this workstation, or re-initializing the feature. The lock is useful when the workstation has been lost, stolen, or compromised.
Unlocking a workstation.
Deleting a workstation → this removes the workstation from the list. It will need to be re-initiated.
Deleting a connector without deleting workstations may prevent any new initialization of these workstations.
User experience
Standard use case
Here is the scenario of a standard authentication. A “Standard authentication” means that the user’s workstation has internet access. Thus, the user is able to receive a notification on Authenticator application and authenticate.
If the TrustBuilder Windows Logon feature is activated and configured in the admin console, the feature activation on the user’s workstation is done automatically and silently at first opening of a windows session with a valid authentication.
The user enters the Windows credential. In this example, the user Bob White selects TrustBuilder MFA (the TrustBuilder credential provider) from the sign-in options. He should enter his Windows password.
.png?inst-v=3deda485-6e03-414c-a98c-84a1ab84ee1e)
The user receives a notification on TrustBuilder Authenticator application to authenticates. In this example, Bob authenticates via his mobile Authenticator application.
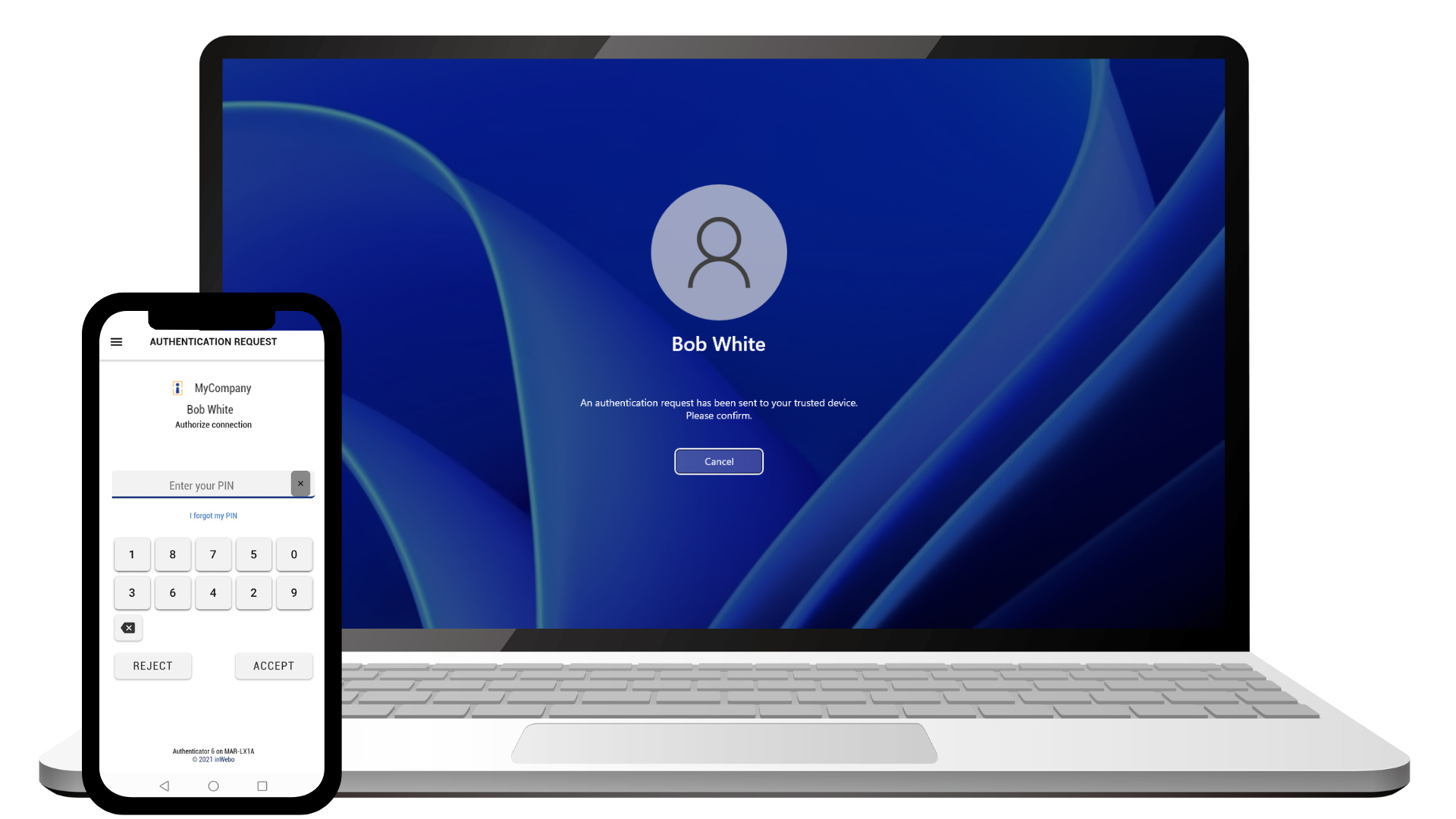
Once authenticated, the session is opened.
Login as a domain user
If the domain is already selected, you can login using your samAccountname.
Example: the user enters “bob.white” to log in as bob.white in the Acme domainIf the domain is not selected, the user can specify the domain using the DOMAIN\user syntax
Example: the user enters ACME\bob.white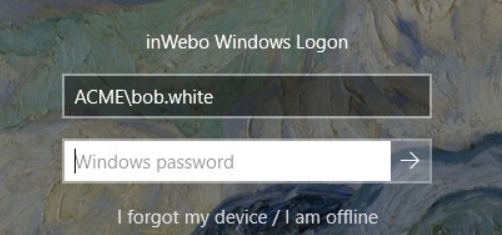
The UPN syntax bob.white@acme.com is not yet supported.
Specific use cases
Offline / No network
The offline mode can be used when a user does not have access to internet (airplane mode for example). In this case, the user has two options to access their Windows session: generate a code with their own Authenticator mobile app or request a code from the administrator/help desk.
To access their Windows session while being offline:
From the Windows login portal, the user click on “I forgot my device / I am offline”.
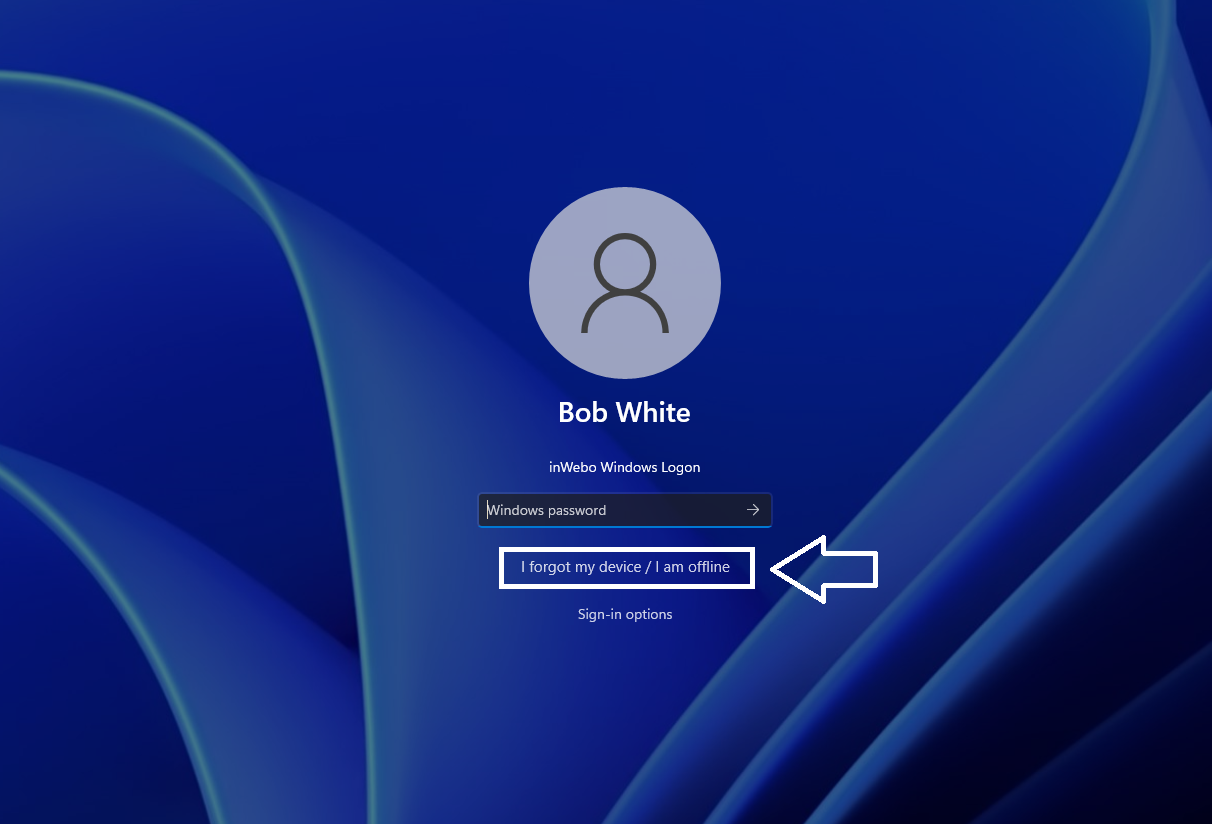
Bob enters a scratch code and his Windows password.
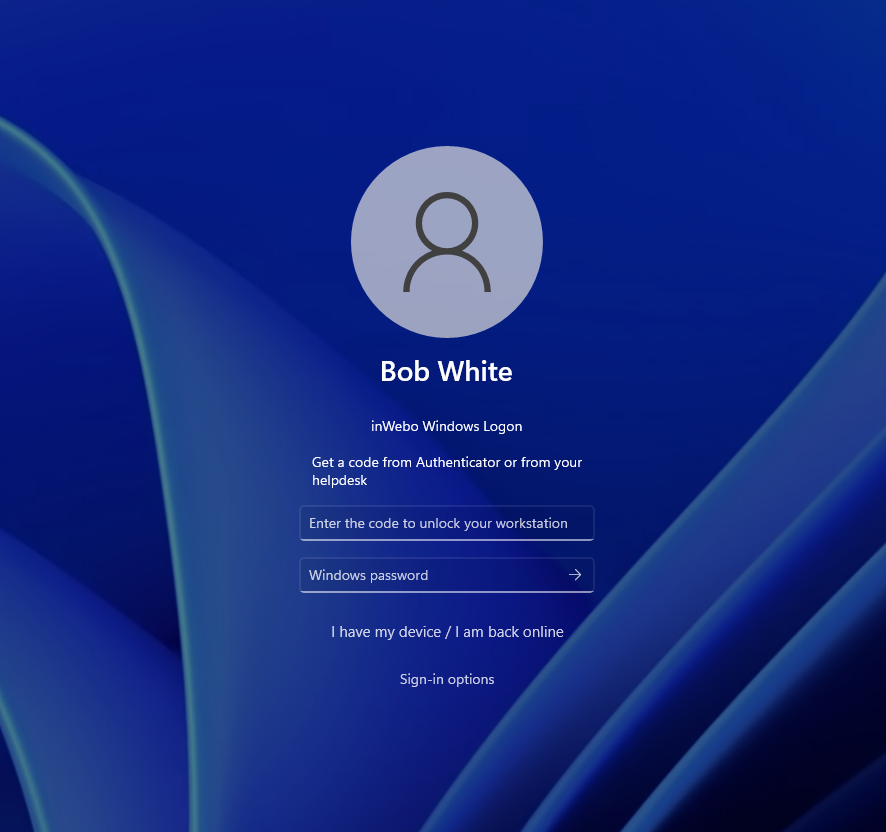
The Windows session is open.
“I forgot my phone”
This specific use-case refers to the situation where the user does not have their phone. Note that the behavior is almost the same as the “Offline mode” use case. The difference is that the user cannot generate a code with their own Authenticator mobile app because we assume that they do not have a phone. In this case, the only option for the user to access their Windows session is to request a code from their administrator/helpdesk.
To access their Windows session without a phone:
From the Windows login portal, the user clicks on “I forgot my device / I am offline”.

Bob enters a scratch code and his Windows password.

The Windows session is open.
Current limitations
The current delivery does not support the following cases:
The credential provider is in English only. Other languages will be supported later.
Microsoft accounts are not supported. In case of a Microsoft account, TrustBuilder MFA is not applied. The behavior is the following: the user enters the Windows password and then the session opens.
Only for local Windows accounts → the following security policy settings (Windows10) are not supported:
“Interactive logon: don’t display username at sign-in”. This setting may be in use to hide user information for shared and sensitive workstations.
“Interactive logon: don’t display last signed-in” is not supported.
In offline or ‘forgot my phone’ case, the scratch code will open the session only once. Later on the user will be able to define a temporary PIN
Offline mode parameters such as the number of scratch codes, their validity and renew frequency are not yet customizable by the administrators
The use of an HTTP proxy for TrustBuilder Windows Logon traffic is not supported
Known issues
These identified known issues will be fixed and will be removed from this list as soon as they are fixed.
Minor cosmetic issues in the credential administration
Troubleshooting
Read the Troubleshooting documentation. This helps identify and solve issues that you may encounter when using TrustBuilder Windows Logon.