TrustBuilder Authenticator - Version 6 (mobile and desktop apps)
This documentation refers to TrustBuilder Authenticator 6 installation and configuration.
The latest version, TrustBuilder Authenticator 7.0, is now available on Android and iOS. Check out the release note for more details.
The legacy Authenticator 4 application is no longer supported and is deprecated.
See Migrating from Authenticator 4 to Authenticator 6
TrustBuilder Authenticator is a One-Time Password generator App that supports push notifications as well a fully offline mode. The main terms you may encounter are the following:
Activation → action of enrolling, registering a device as a trusted authentication tool.
Device → trusted authentication tool. It may be a mobile, a computer (desktop app) or a web-browser.
OTP → the One-Time Password you can generate to log in.
Service → the environment in which your account is registered. It is usually your company.
Account → the space where your personal data is stored as a user in a service. You access your account settings from your Authenticator application.
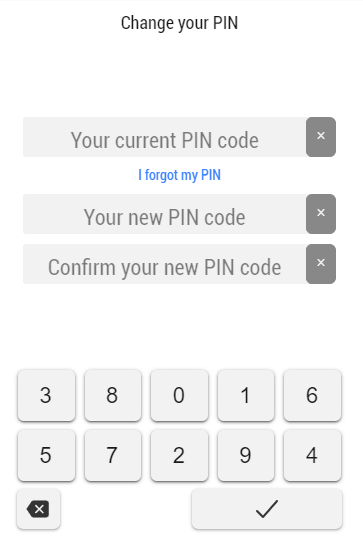
PIN code → the personal identification number (PIN) used for authentication. It is also required to validate an important action in your account.
Installing Authenticator app
TrustBuilder Authenticator App is available for the following operating systems:
Android
Download TrustBuilder Authenticator for Android → Google Play Store
iOS
Download TrustBuilder Authenticator for iOS: App Store
MacOS
Download TrustBuilder Authenticator for iOS → App Downloads page
Windows
Download or deployment
You can chose between a few deployment methods and packages:
Users may download the exe file from the App Downloads page
Users may install it directly from the Windows Store
Note: to set Authenticator app to start automatically on Windows startup, the user must start it manually at least once
Administrators may want to deploy it automatically to your users via GPO. You can find the msi file for scripting and deployment in the Resources Downloads.
Notifications are not working for new installations of Authenticator 6 on Desktop, for versions below 6.38
The issue is fixed in Authenticator 6.38
Install the app certificate
Note: The certificate is used for admins connecting to the Admin Console V2 using desktop Authenticator. There are two ways to install the certificate.
Install the certificate by launching the app as administrator
Install Authenticator manually with exe, with a non admin user
Close Authenticator.
Launch Authenticator as an administrator, by right clicking on the icon. This installs the certificate
The following application launches can be done with a non admin user.
or
Install the certificate manually
Install Authenticator application and launch it.
Save the certificate in a folder on the local computer. The certificate is available in the “About” page of your installed Authenticator 6 App.
Rename the file in .crt format
Right click and select "Install certificate"
Select "open" and "Local Machine" in the Certificate Import Wizard screen
Select "Next" and "Place all certificates in the following store"
"Browse" Certificate store" and select "Trusted Root Certification Authorities"
Select "OK", "Next" and "Finish".
Silent installation
The TrustBuilder Authenticator application can be silently installed. Run the following commands with admin privileges: "Authenticator-Windows-Setup.exe" /S
Error codes
TrustBuilder Authenticator installer returns error codes as a result of their execution:
0 - Normal execution (no error)
1 - Installation aborted by user (cancel button)
2 - Installation aborted by script
Upgrading the Authenticator app
Our recommendations when upgrading Authenticator on Windows are the following:
Install the new version without uninstalling the previous one. This will allow you to keep the activated accounts of your Authenticator devices. If you uninstall your Authenticator application, you will lose the TrustBuilder MFA profiles activated on these tools.
Keep the same installation method (exe or msi or Windows Store) as the one used to install the previous version. EXE files, MSI installers and Windows Store installation use different installation paths. For example, upgrading exe to msi will not keep your users' enrollments.
To see if you have previously installed via the exe or via the msi, check the Authenticator 6 installation directory:
for the exe, the installation directory is: C:\users\<User_Name>\AppData\Local\Programs\authenticator6
for the msi, the installation directory is: C:\Programmes(x86)\Authenticator 6
To upgrade to Authenticator 6.14, you should upgrade from 6.12 only. Upgrading from Authenticator 6.8 to Authenticator 6.14 is not possible.
Proxy
Authenticator for Windows will use the PROXY - HTTP_PROXY - HTTPS_PROXY environment variables when they are defined. To ignore any proxy settings, you can add the environment variable NO_PROXY with any value (supported from Authenticator 6.26.0).
Linux
TrustBuilder Authenticator for Linux is delivered in AppImage format. This format is compatible with a wide range of 64-bits Linux distributions, however TrustBuilder is using the latest version of Ubuntu LTS as a reference platform. The reference platform is used by TrustBuilder as follows:
The app is validated by TrustBuilder on the reference platform
If an issue is reported, TrustBuilder will use the reference platform to reproduce and fix the issue
The AppImage format will ensure compatibility with other Linux distributions
Download
Download TrustBuilder Authenticator for Linux here → Resources Downloads
Prerequisites
The Keyring package is mandatory as it is used to store the user secrets in the user keychain.
If the package is not present, you can install it usingsudo apt install gnome-keyring.
When launching the application, the Keyring must be unlocked by the user.AppImages require FUSE version 2 to run. Depending on the Linux distribution you are using, you may have to install it. You can install it using
sudo apt install libfuse2. For more information see FUSE.
Installation
To run TrustBuilder Authenticator application for Linux you should:
Make the TrustBuilder_Authenticator6.AppImage file executable:
Right-click on the file > Properties > Permissions > Enable “Allow executing file as a program”
orRun the following command:
$ chmod a+x TrustBuilder_Authenticator6.AppImage
Run the application:
Double-click on the file
orRun the following command:
$ ./TrustBuilder_Authenticator6.AppImage
Notes and Tips
The reference platform Ubuntu LTS is available for 64-bits only
Automated launch at session opening is possible with a command-line, see AppImage documentation . You can also use AppImage Launcher.
When launching the application, the Keyring must be unlocked by the user.
The deeplinking (direct link to an application page) is not yet available on Linux
When uninstalling TrustBuilder Authenticator for Linux, you will have to delete the folder
~/.config/Authenticator 6manuallyThe connection to the Admin Console v2 with Authenticator for Linux is not supported. Administrators with a Linux workstation can use Virtual Authenticator.
Network prerequisites for notifications
Context
TrustBuilder Authenticator uses Google’s Firebase Cloud Messaging (FCM) services to register devices and deliver notifications to these devices. If you are using notifications, and if your organization uses a firewall to restrict traffic to or from the Internet, you need to configure it to allow mobile or desktop devices to connect with FCM.
Notes:
To receive notifications, TrustBuilder Authenticator opens and maintains a session to FCM on one of the following remote ports: 5228,5229 or 5230. The IP address used by Authenticator for the notification mechanism belongs to block ASN 15169 (Google)
These notifications do not contain security content. The content of notifications are the same for the desktop application and the mobile application.
The notification process is a way to improve the user experience of starting the authentication. It is possible to not use notifications, and use the feature “Authorize a connection” or “Pending operation” in Authenticator to retrieve the authentication request and proceed to the authentication.
Minimum requirements
The very minimum requirements are to allow:
firebaseinstallations.googleapis.com on port 443 (TLS)
fcmregistrations.googleapis.com on port 443 (TLS)
fcm.googleapis.com on port 443 (TLS)
android.clients.google.com on port 443 (TLS)
mtalk.google.com on port 5228, 5229 or 5230
Related documentation
Our recommendation is to apply the official Firebase network prerequisites by Google. This is documented here and may vary over time: https://firebase.google.com/docs/cloud-messaging/concept-options#messaging-ports-and-your-firewall
Authenticator app User guide
Download TrustBuilder Authenticator application
First app launch
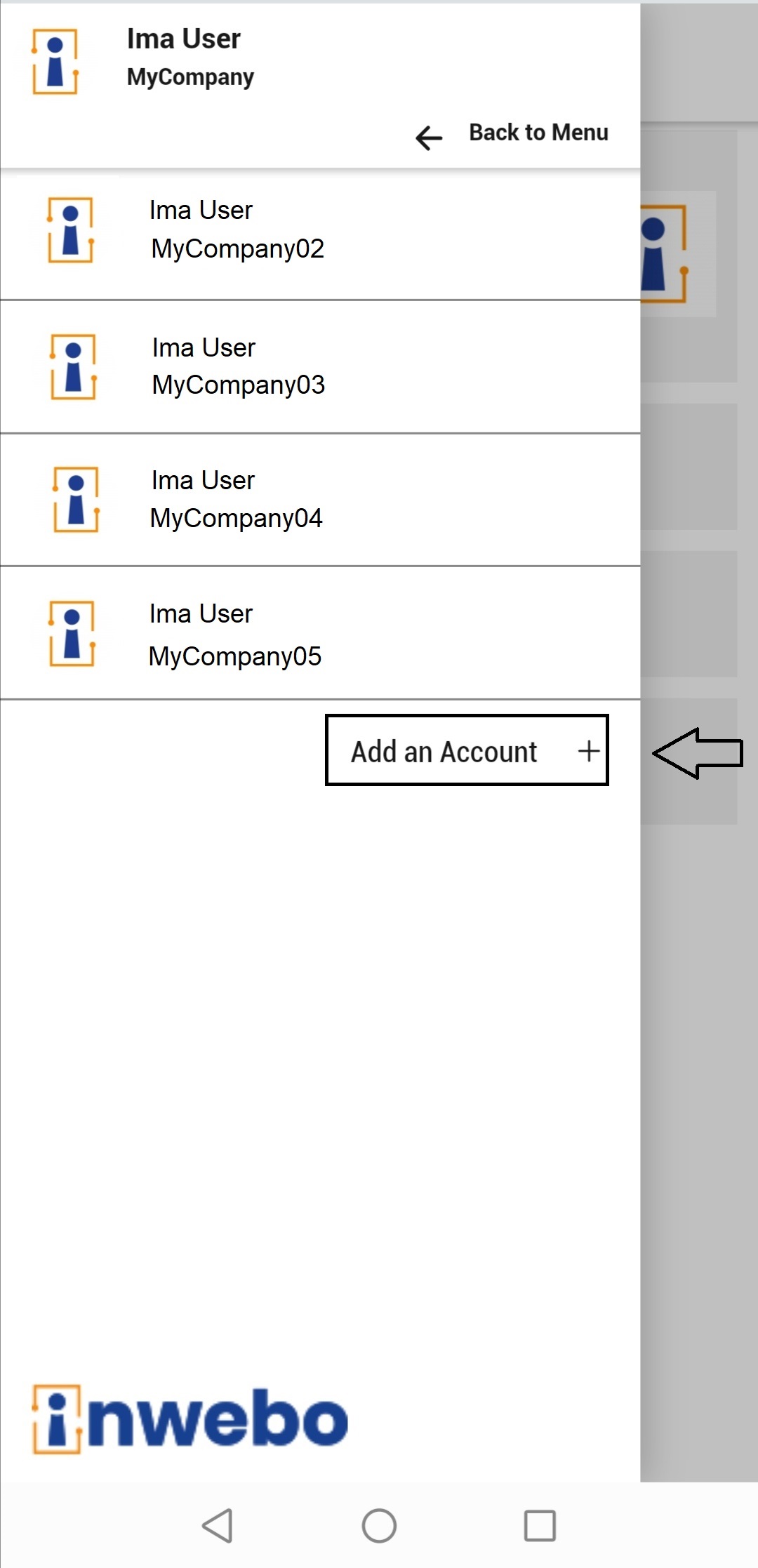
To get started with Authenticator 6 app, you should first add a new account.
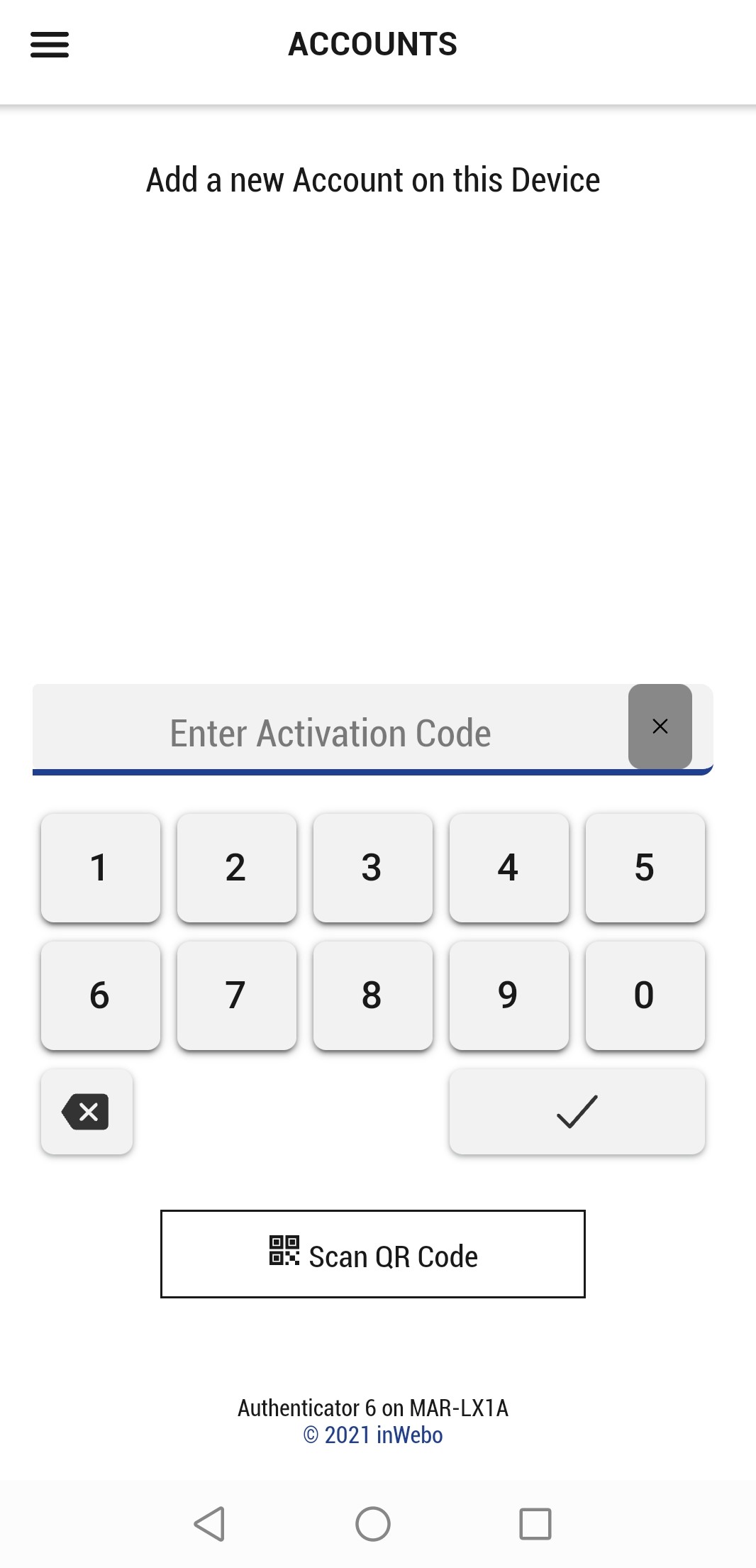
Prerequisite: an activation code (contact your administrator)
Launch TrustBuilder Authenticator application.
Check “I agree” to give your consent to the Privacy Policy.
Allow Authenticator to take pictures (this is used to scan QR codes).
Enter a valid activation code and click the validate button.
To get a valid activation code for the first time, contact your administrator.Define a new PIN code.
You have successfully added your account. Your device is now activated as a trusted device. You can use it for authentication.
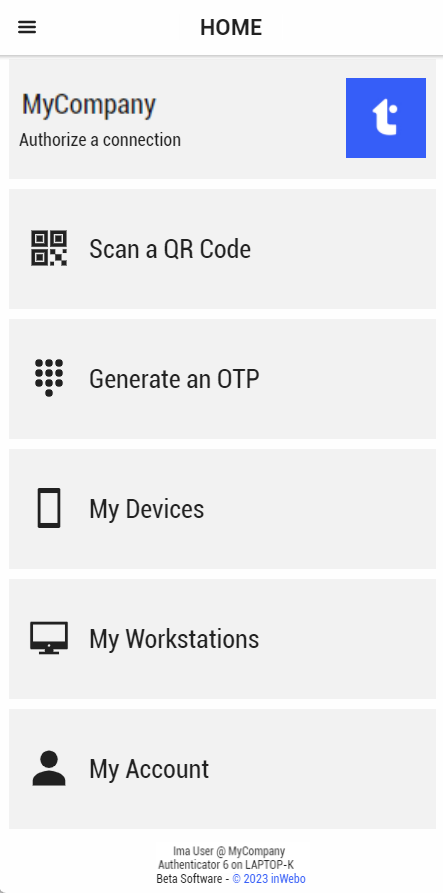
Overview
From the home page you can perform several actions:
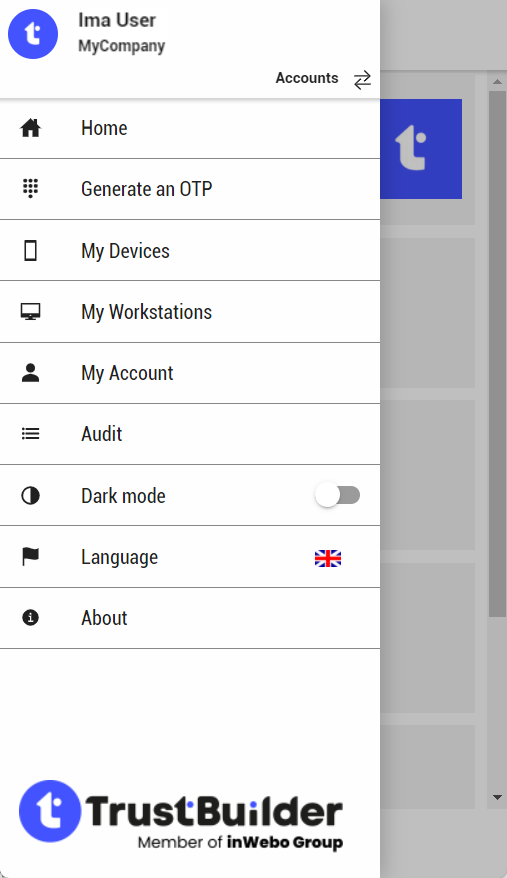
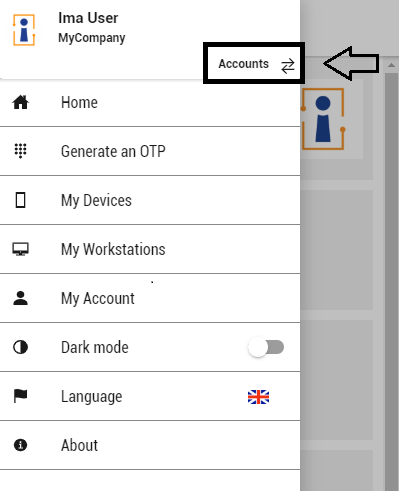
Click on the top-left three stacked lines (hamburger menu) to display the hidden left menu. From the left menu you can perform other actions.
Authentication with the app
There are several methods to authenticate using TrustBuilder Authenticator app. Depending on the service parameter configuration, you may be able to authenticate with the following methods: push notifications, QR code scanning and OTP generating.
Receive a push notification
You will receive a push notification trough TrustBuilder Authenticator app. Push notifications can be sent automatically or triggered manually, depending on configuration. You should then approve or reject the pending operation. Each approval operation is protected by PIN code or biometric (except for services without PIN).
On the authentication page, click OK to trigger the push notification.
This step may not occur depending on the configuration. The push notification can be sent automatically.Click on the notification to open the application.
.gif?inst-v=08adbb31-d621-42e6-a87d-1cb2c2f1e144)
Accept or reject the authentication request.
Enter your PIN or provide biokey if requested.
Scan a QR code
(from TrustBuilder Authenticator 6.31)
The authentication page displays a QR code that you should scan with TrustBuilder Authenticator app. You should then approve or reject the pending operation. Each approval operation is protected by PIN code or biometric (except for services without PIN).
Go to “Scan a QR Code”.
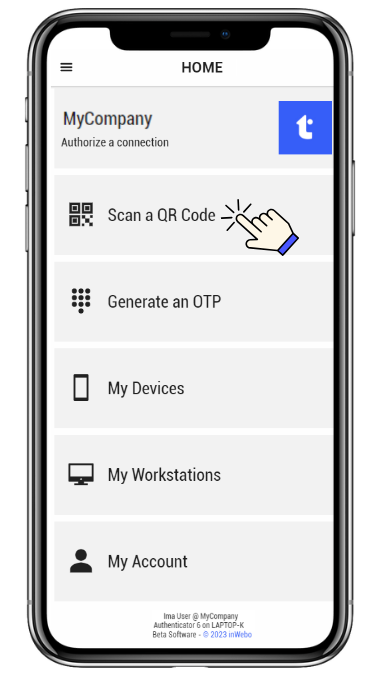
Scan the QR code displayed in the authentication page.
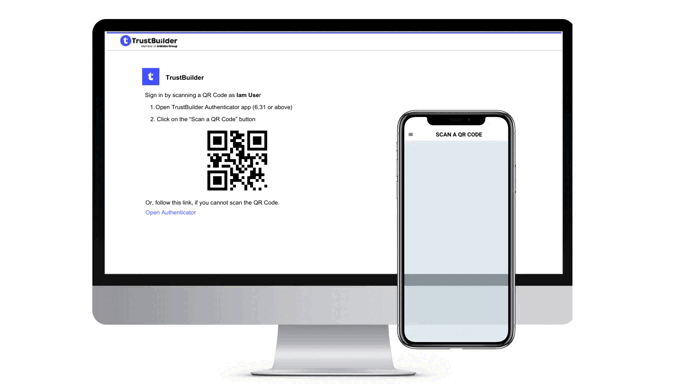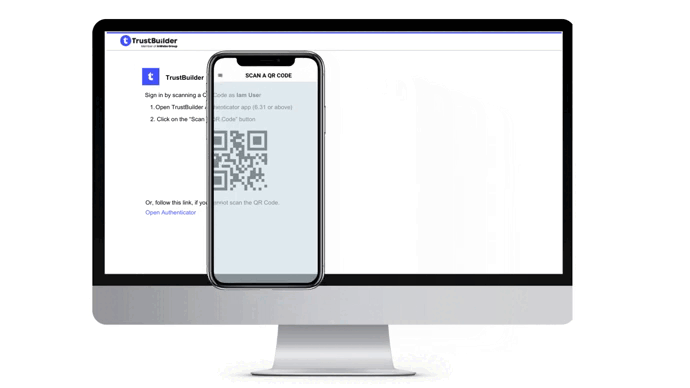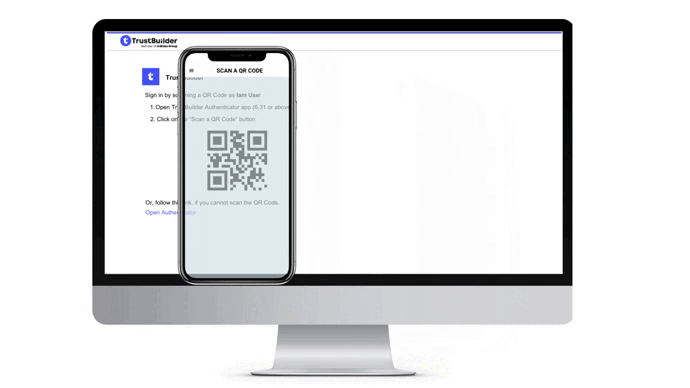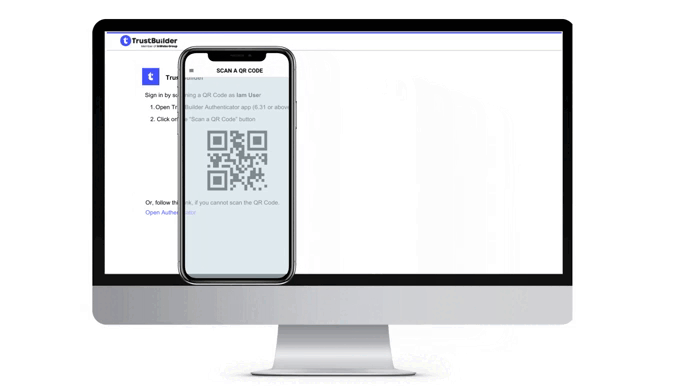
If you cannot scan the QR code, click on the Open Authenticator link on the authentication page. It will open the Authenticator app.
Accept (or reject) the authentication request.
Enter your PIN or provide biokey if requested.
Generate a One-Time-Password (OTP)
Generate a One-Time-Password (OTP) in TrustBuilder Authenticator app. The generated OTP should be manually entered in the TrustBuilder MFA authentication page. You have 30 seconds to input the OTP before it generates another. Each OTP generating operation is protected by PIN code or biometric (except for services without PIN).
Go to “Generate an OTP”.
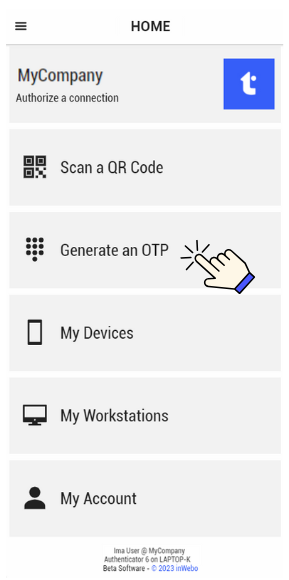
Enter your PIN or provide biokey if requested to get an OTP.
On the authentication page, enter the OTP and click on OK.
You have 30 seconds to input the OTP before it generates another.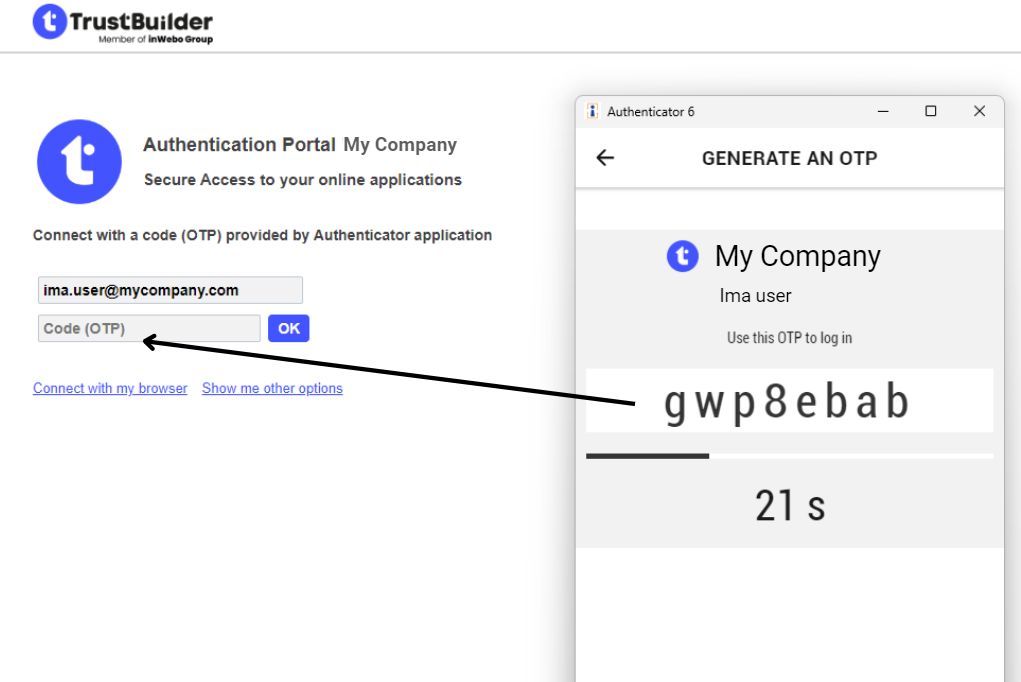
Configuration
My Account
My Devices
From TrustBuilder Authenticator home page, go to My Devices. It displays a list of the trusted devices registered for your account.