Wallix Bastion LDAP configuration
This integration add inWebo MFA to an existing Wallix AD integration. User will authenticate by providing his AD credentials then he will receive a notification on his inWebo Authenticator application installed on his mobile or desktop.
Wallix Bastion configuration
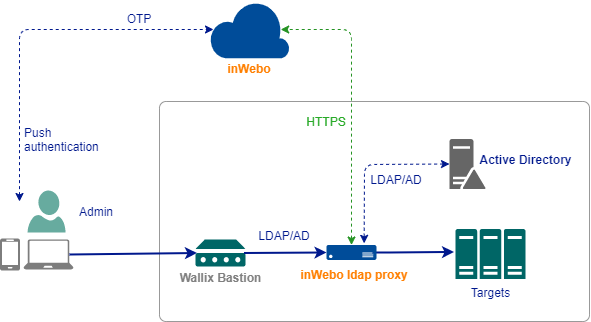
Create an external AD authentication source
In "Configuration/External Authentication" menu click "Add an authentication". Most of parameters values are the same as if you were directly targeting an Active Directory or LDAP.
Make sure you provide a Distinguished Name for the "User" parameter, entering only a login will not work properly.
With version <6.2
Select "LDAP-AD" and enter your inWebo ldap-proxy IP and port.
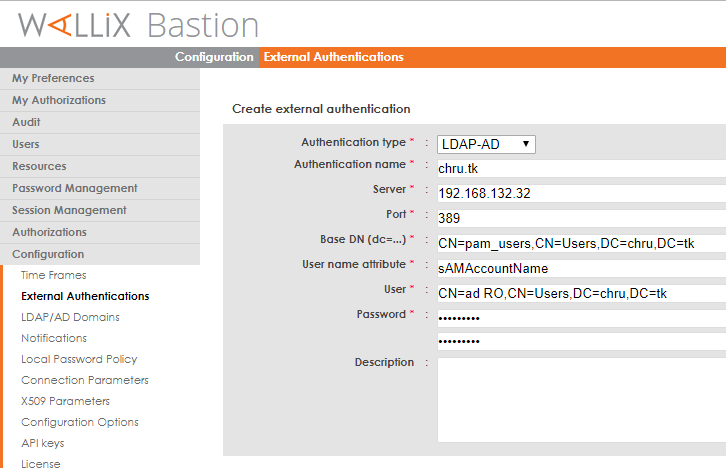
With version >= 6.2
Select "LDAP" and enter your inWebo ldap-proxy IP and port. Set a 30 seconds timeout or more so your users will have time to validate the MFA notification.
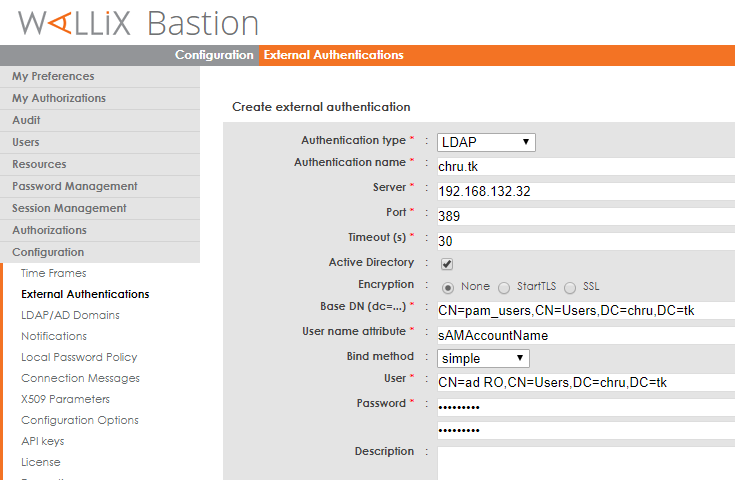
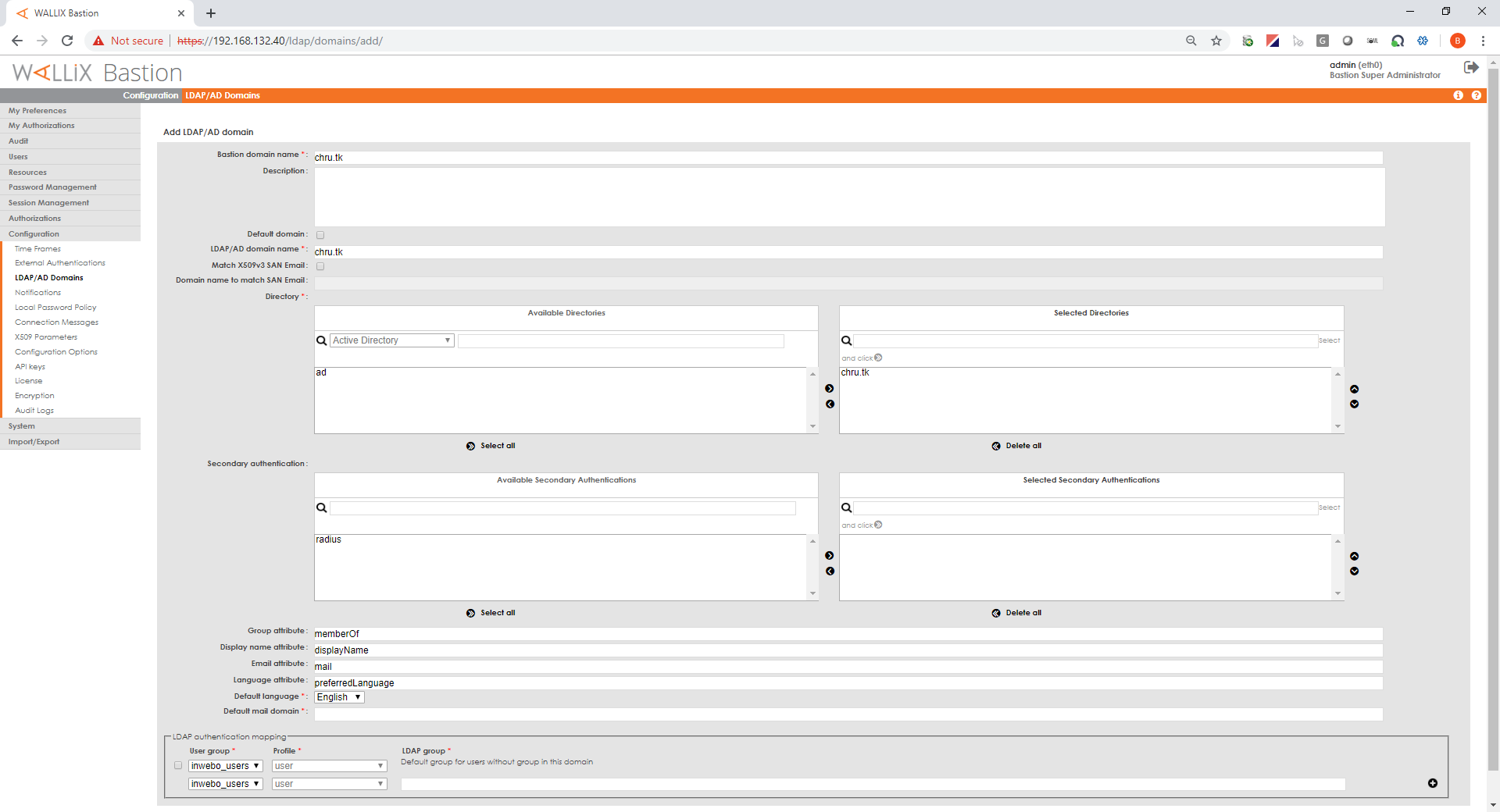
Create an AD domain
In "Configuration/LDAP/AD domains" menu click "Add a domain".
If you deploy on a production infrastructure, make sur the AD ldap domain name is not already used. For testing you can use any value you want (test.com), then you'll have to login to the bastion using sAMAccountName@test.com as username.
With version <6.2
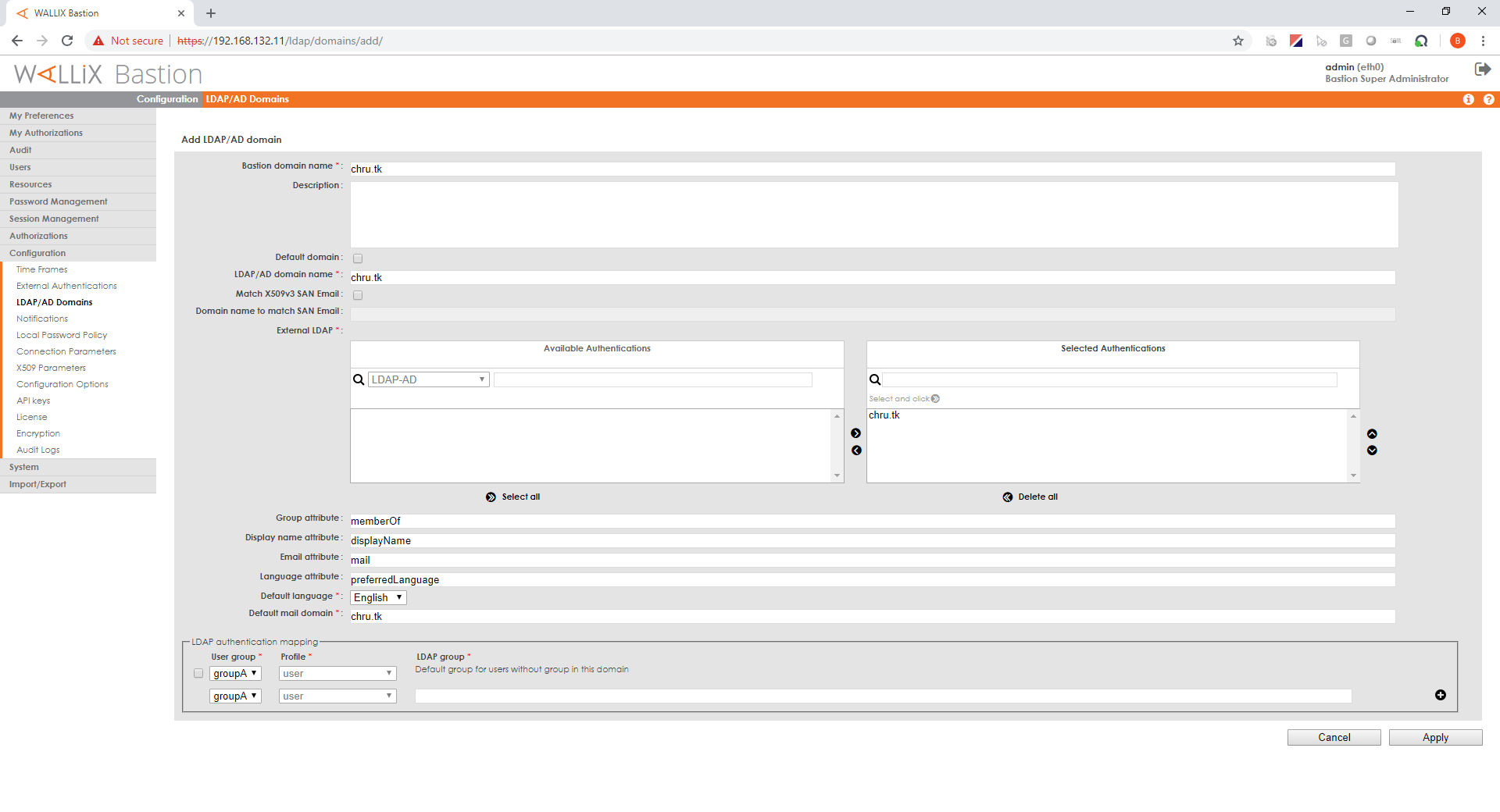
With version >=6.2
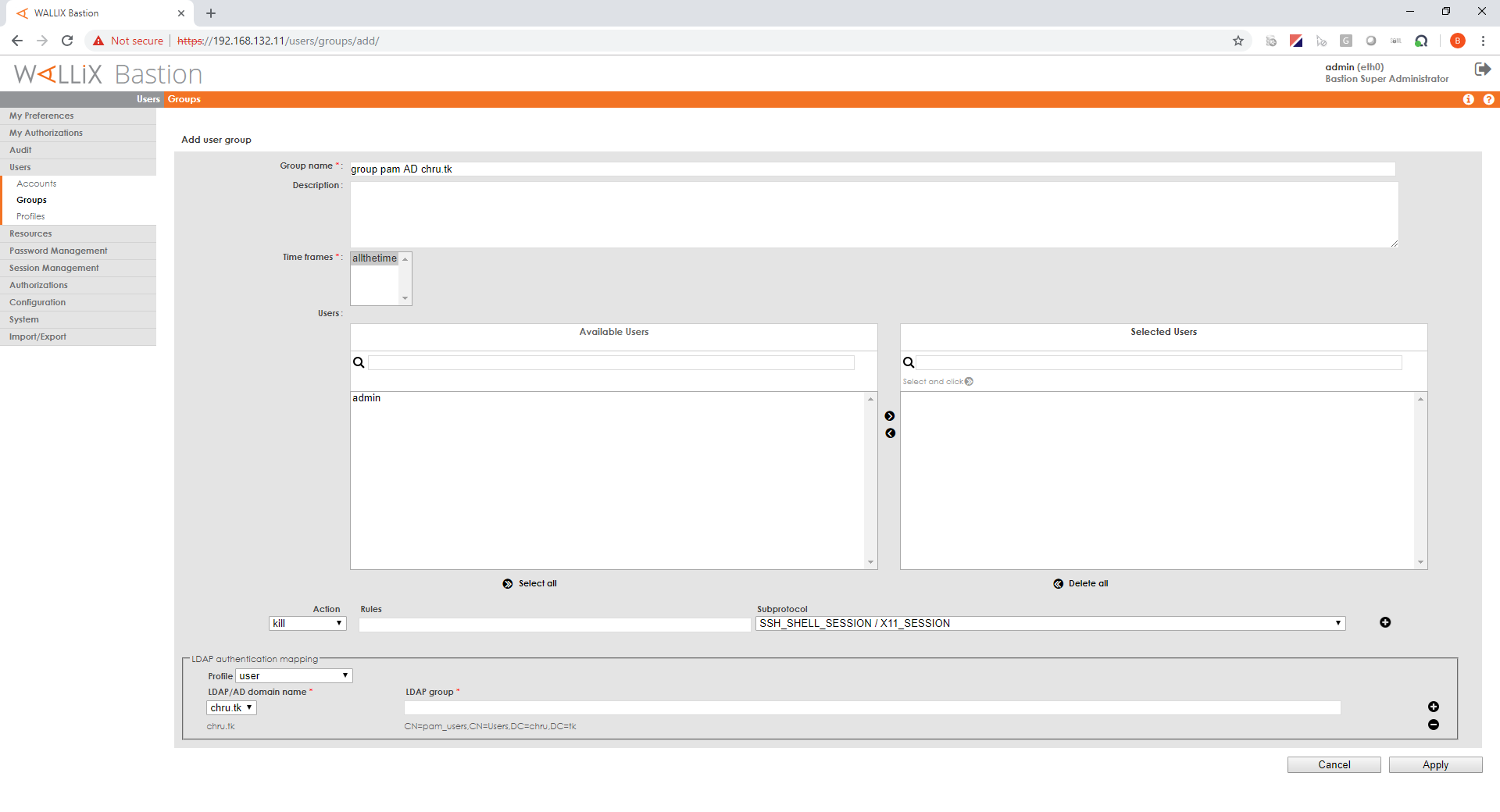
Create a user group
In "Users/Groups" menu click "Add a group"
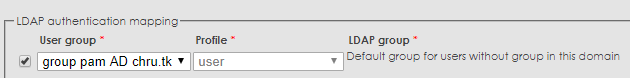
Back in AD domain configuration check the group is by default assigned to your AD users or make sure this group is associated with the LDAP group you want to map.
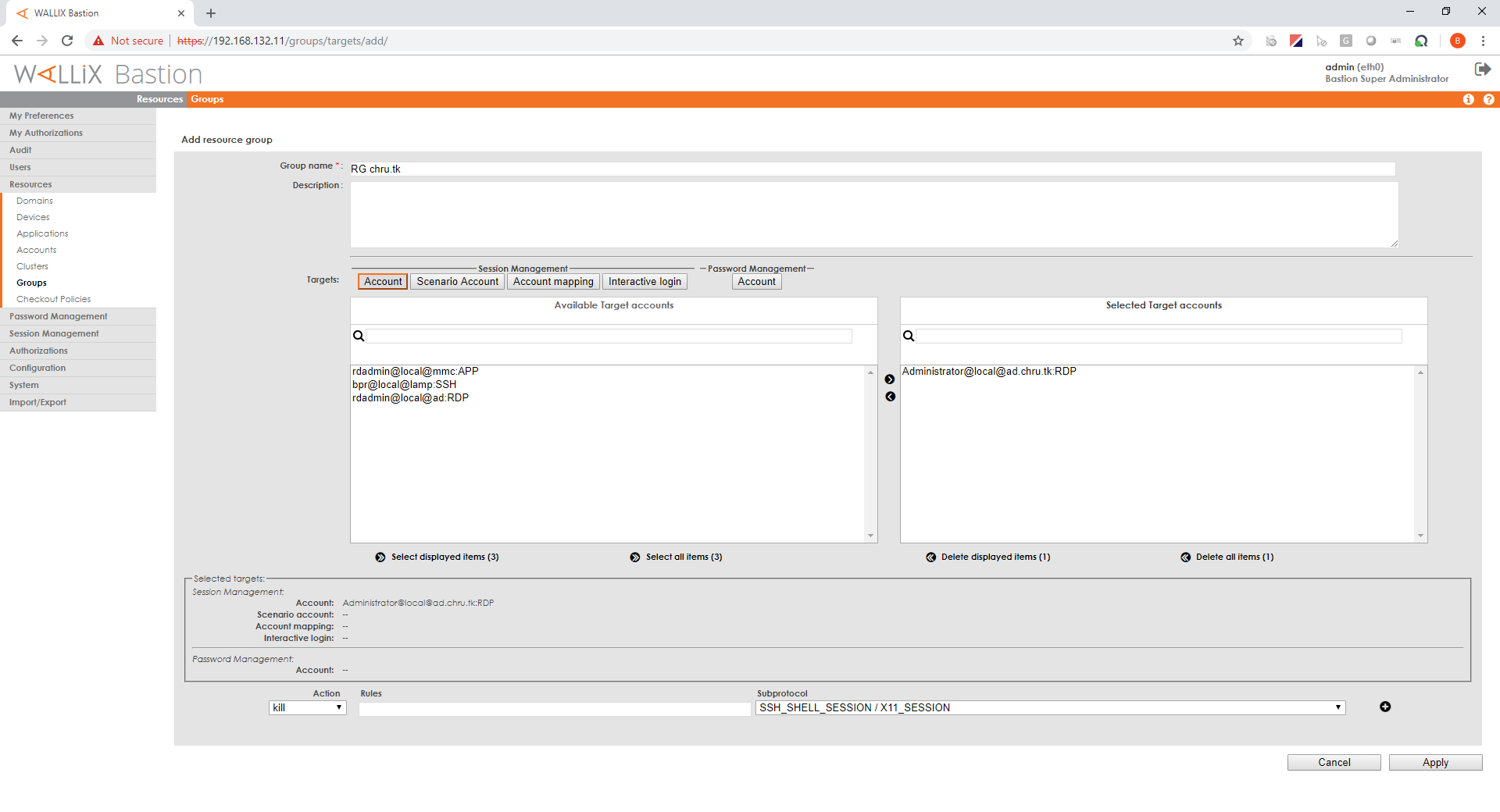
Create a resource group
In "Resources/Groups" menu, click "Add a group".
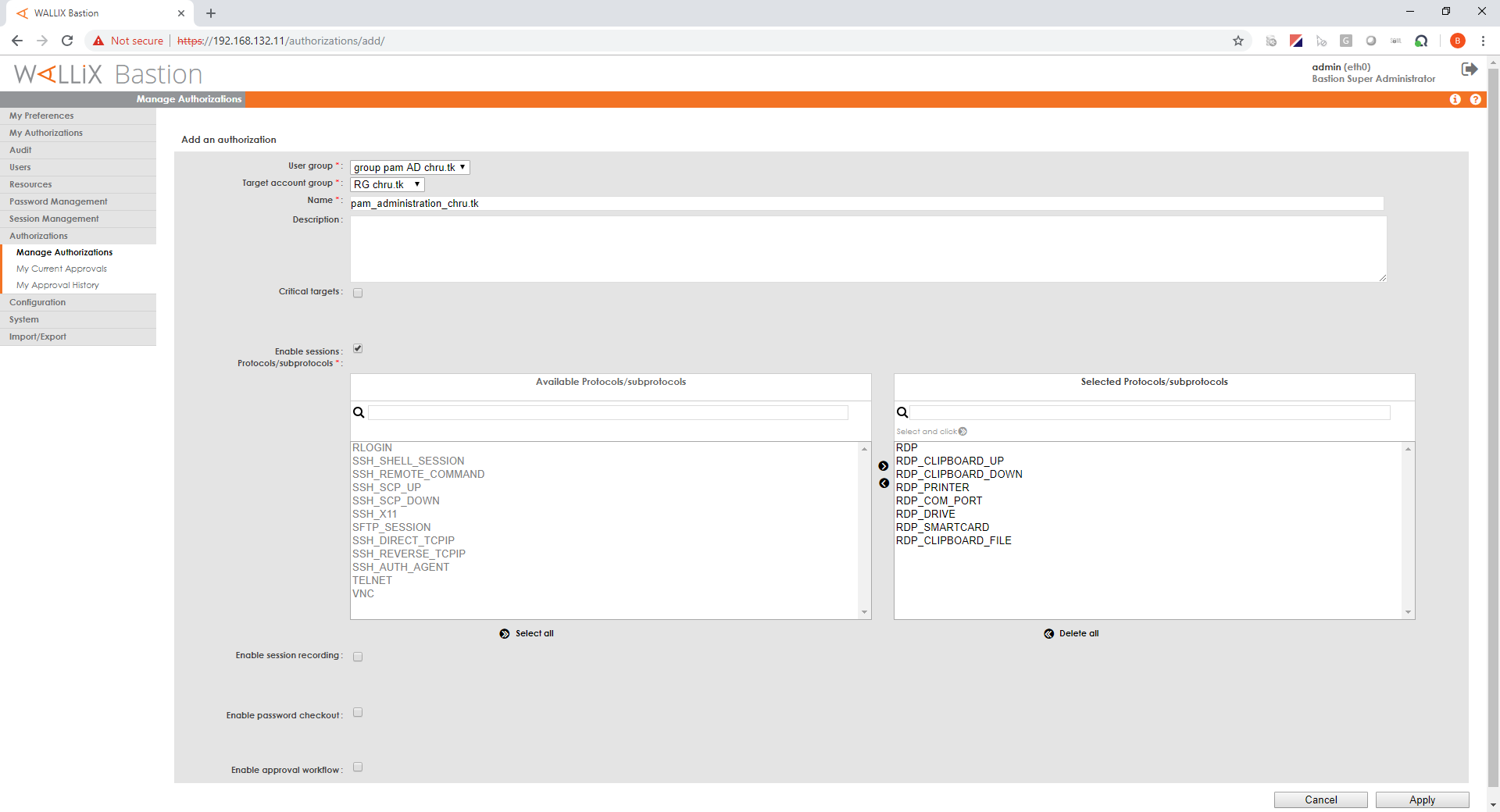
Add authorization
In "Authorizations/Manage Authorizations" menu, click "Add an authorization"
Change the default ldap timeout
With version <6.2
In "Configuration/Configuration Options" menu, select "WabEngine"
Change "Ldap auth timeout" value to 60.0. This will give 60 seconds to your users to answer a push authentication.
With version >=6.2
The ldap timeout is set on each External authentication (See above)
inWebo LDAP Proxy configuration
inWebo LDAP Proxy installation and configuration guide is here: inWebo LDAP Proxy v1.0.0
Configure your ldap proxy with
certificat path and its passphrase
inWebo service ID
Ldap server IP and port
whitelist DN : provide the DN for the read only account configured on the "external AD authentication source"
login attribute : sAMAccountName and userPrincipalName are often used when integrating with AD but you can change it to something more relevant to your architecture
Typical configuration sample
config.properties sample
###############################
# LDAP Proxy configuration file
###############################
# Once complete, you must rename this file as config.properties
##################################
# LDAP PROXY CONFIGURATION SECTION
##################################
# Listening IP adresses used by the LDAP proxy
# List of IP/hostname separated by ";"
# All local addresses by default
ldap.proxy.addresses=192.168.132.4
# Listening port for the LDAP proxy
ldap.proxy.port=389
# Listening port for the LDAP proxy to handle LDAPS requests
#ldap.proxy.ssl.port=636
# LDAP server address/hostname
ldap.host=192.168.132.32
# LDAP server port
# Required if ldap.proxy.port is set
ldap.port=389
# LDAPS server port
# mandatory if ldap.proxy.ssl.port is specified
#ldap.ssl.port=636
######################################
# INWEBO SERVICE CONFIGURATION SECTION
######################################
# InWebo service ID
inwebo.service.id=1111
# full path to the p12 certificate associated with the InWebo service
inwebo.service.certificate.path=/usr/share/ldap-proxy-1.0.0/config/inwebocert1111.p12
# inWebo certificate passphrase
inwebo.service.certificate.passphrase=HYtsPuRWzG3awo1k2gY4
# LDAP attribute for user login (will be matched with InWebo login)
# uid by default
#ldap.proxy.login.attribute=displayName
ldap.proxy.login.attribute=sAMAccountName
#ldap.proxy.login.attribute=userPrincipalName
# Condition to authenticate users with InWebo
# all by default
# all : all user will be authenticated with inWebo
# none : no user will be authenticated with inWebo (transparent)
# user : user group membership. Based on the group list the user is member of
# group : user group membership. Based on the group member list
ldap.proxy.do.step.up.by.type=all
# LDAP group DN for which members will be required to authenticate with inWebo. Required if ldap.proxy.do.step.up.by.type is set to "user" or "group"
#ldap.proxy.do.step.up.group.base.dn=
# LDAP attribute for group members. Required when ldap.proxy.do.step.up.by.type = group
# member by default
#ldap.proxy.do.step.up.lookup.member.attribute=
# LDAP attribute for group list. Required when ldap.proxy.do.step.up.by.type = user
# isMemberOf by default. Use memberOf for AD
#ldap.proxy.do.step.up.lookup.ismemberof.attribute=
# LDAP objectClass attribute used to define a group
# groupOfNames by default
#ldap.proxy.do.step.up.filter.group.object.class=
# LDAP objectClass attribute used to define a user
# person by default
#ldap.proxy.do.step.up.filter.user.object.class=
# Bypass inWebo authentification for a list of users (usefull for technical accounts)
# DN list separated by ";"
ldap.proxy.whitelist.dn=CN=ad RO,CN=Users,DC=chru,DC=tk;
# 16 characters key used to cipher logins
# No cipher by default
#inwebo.cipher.aes.secret.key=
##################################
# INWEBO API CONFIGURATION SECTION
##################################
# InWebo API URL
# https://api.myinwebo.com/FS by default
#inwebo.base.url=
# HTTP proxy host used to call InWebo
# No HTTP proxy by default
#inwebo.proxy.host=
# HTTP proxy port
#inwebo.proxy.port=
# Use https to proxy
# false by default - http only
# true - https only
#inwebo.proxy.https=
# HTTP proxy login
#inwebo.proxy.username=
# HTTP proxy password
#inwebo.proxy.password=