Stormshield (NetASQ) - RADIUS integration
This is the procedure to integrate inWebo multi factor authentication service with "Stormshield" RADIUS authentication.
TrustBuilder strong authentication service supports many built-in interfaces such as RADIUS, SAML 2.0, Web Services API, Google Apps and many more. When working with a network device (firewall, reverse proxy,…) the preferred method is RADIUS. This is what we will explain further in this document.
Configure authentication portal on Stormshield
In this example, we will take for granted that you already have a Stormshield firewall up and running.
You will need to:
Create RADIUS Servers objects
Connect to your Stormshield Administration interface.
Go to Objects > Network
Click on +Add
Create 2 new objects called radius-a.myinwebo.com and radius-b.myinwebo.com:
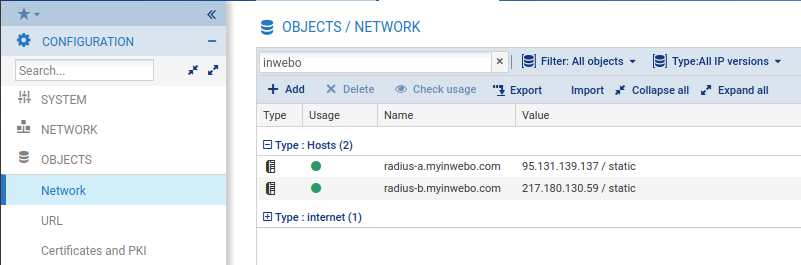
inWebo Radius server addresses :
Primary: radius-a.myinwebo.com (95.131.139.137)
Secondary: radius-b.myinwebo.com (217.180.130.59)
(See RADIUS integration and redundancy for additional details and configuration)
Configure VPN SSL
Go to VPN > SSL VPN.
Set VPN / SSL VPN to ON to enable SSL VPN.
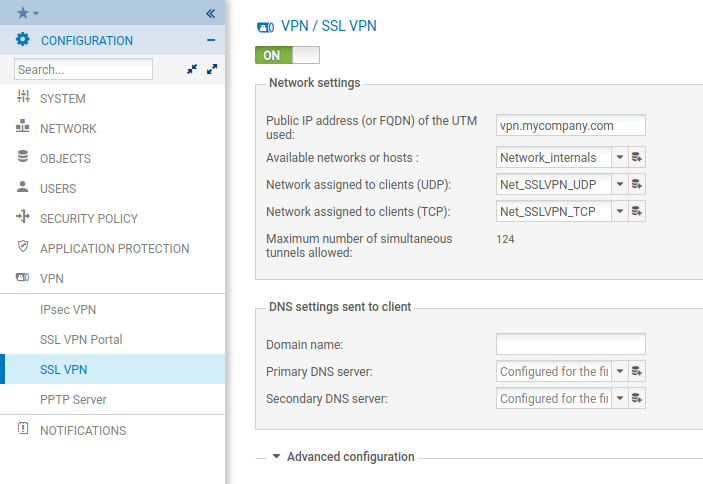
Configure Web Servers, Application Servers and User profiles according to your needs.

Configure Users and Groups to use RADIUS Authentication
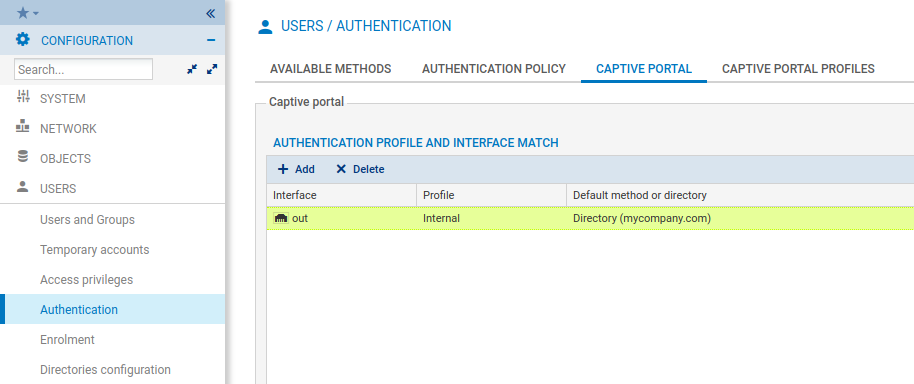
Go to Users > Authentication.
In Available Methods tab:
Click on + Enable a method.
Choose RADIUS.
Configure this authentication method with the 2 RADIUS server objects you created earlier.
Choose the RADIUS secret which will be shared with TrustBuilder MFA servers (this is a string that will be used to cipher the RADIUS requests).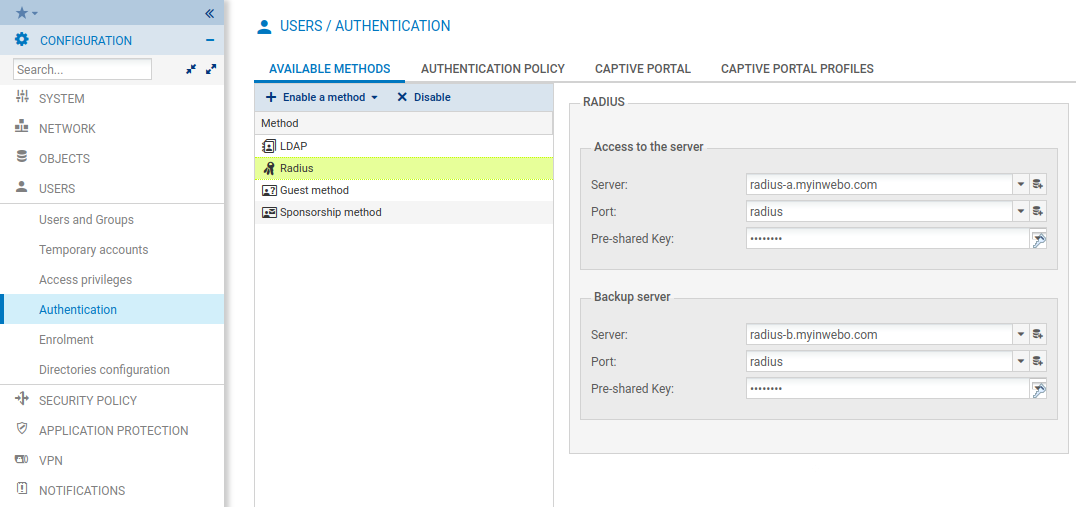
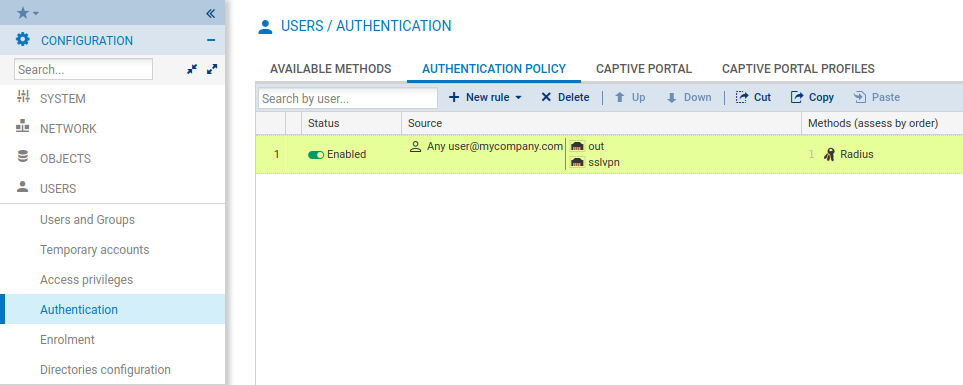
Create a group:
Go to Users > Users and Group.
Add a group. Give it a name (example: inwebo-users).
Insert the users you want.
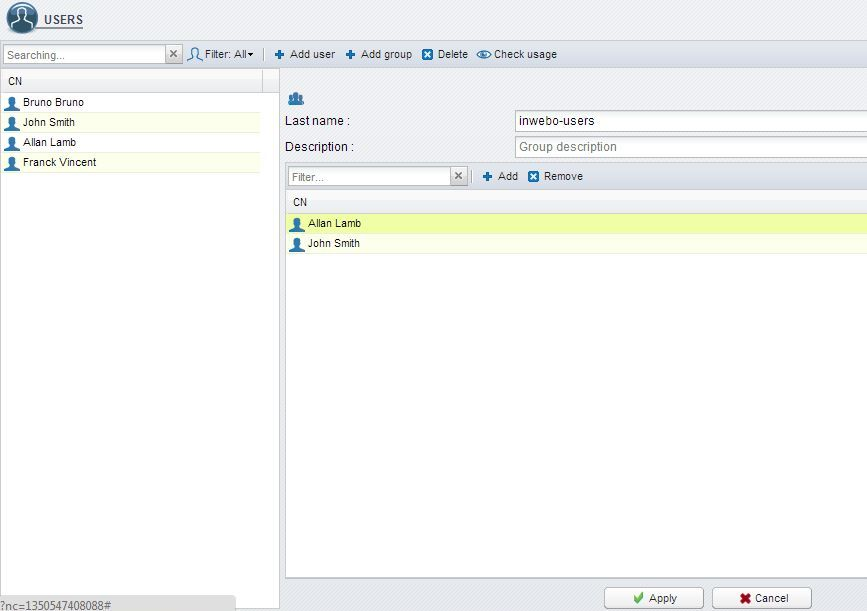
Click on Apply.
Go to Users > Access Privileges.
In Detailed access tab, allow the SSL VPN policy for the group you created to access SSL VPN with RADIUS authentication
Click on Apply.
Set the RADIUS timeout
To set the RADIUS timeout, enter the following command lines:
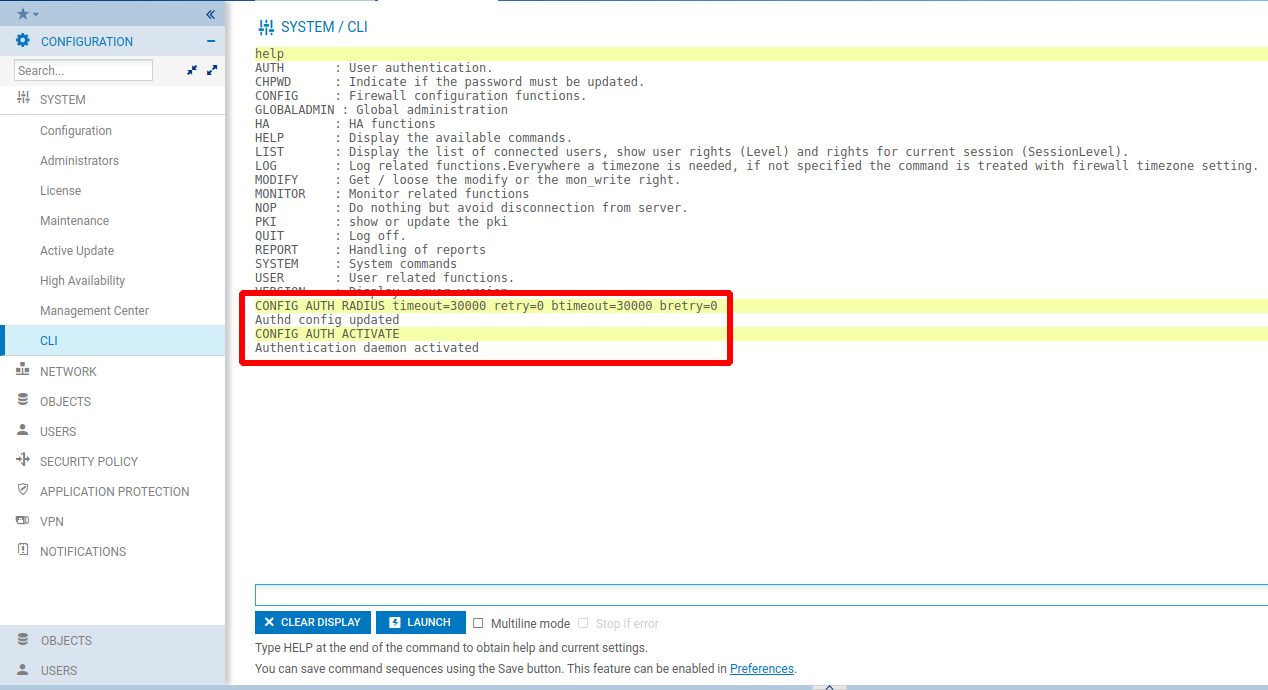
CONFIG AUTH RADIUS timeout=30000 retry=0 btimeout=30000 bretry=0
CONFIG AUTH ACTIVATE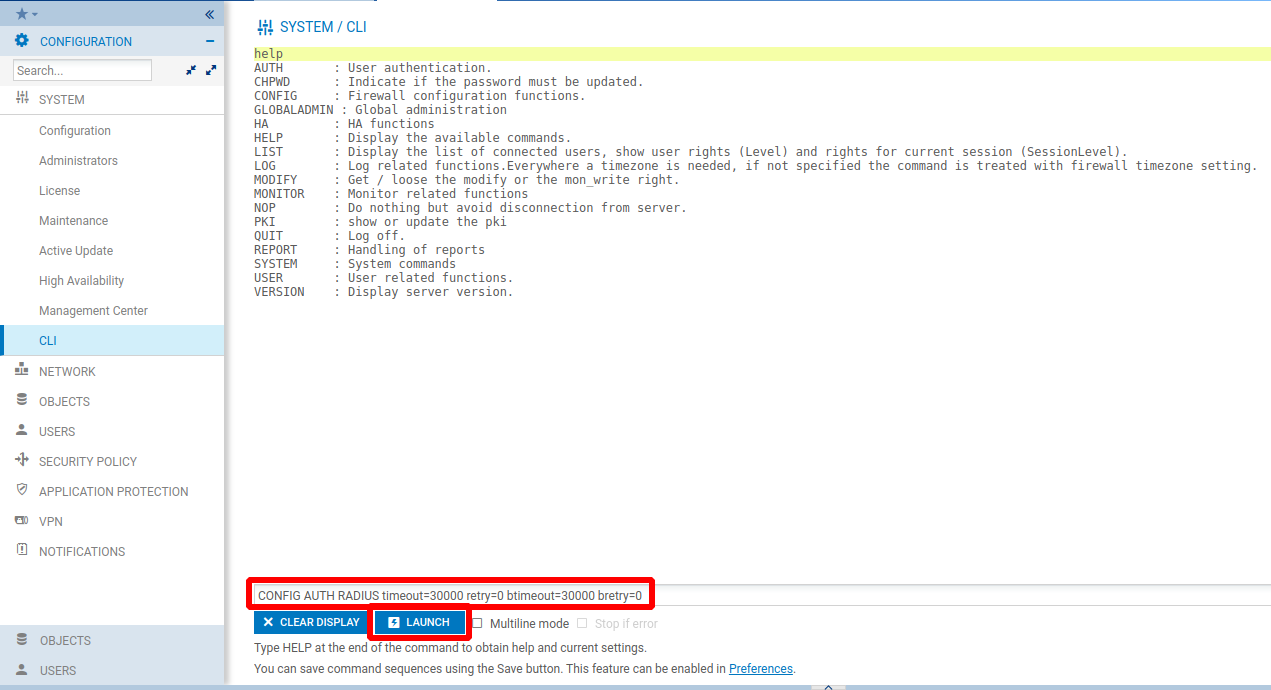
Configure TrustBuilder MFA RADIUS connector
Login to TrustBuilder MFA administration console.
Go to Secure Sites" tab
Select “Add a connector of type…”, and choose “Radius Push”.
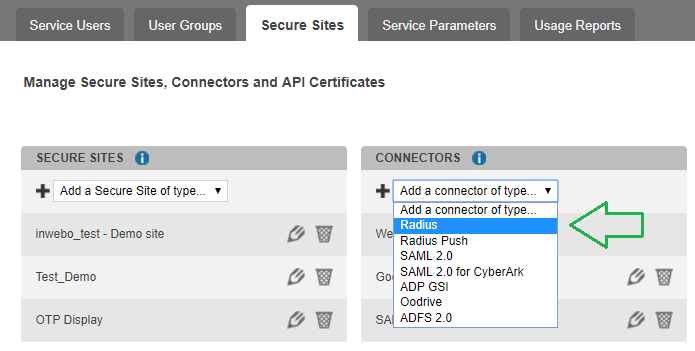
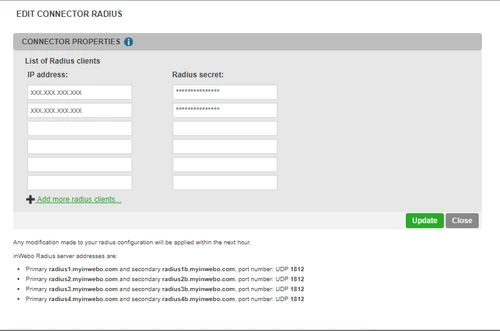
Enter the public IP addresses of your Stormshield servers, along with the RADIUS secret you have defined earlier:
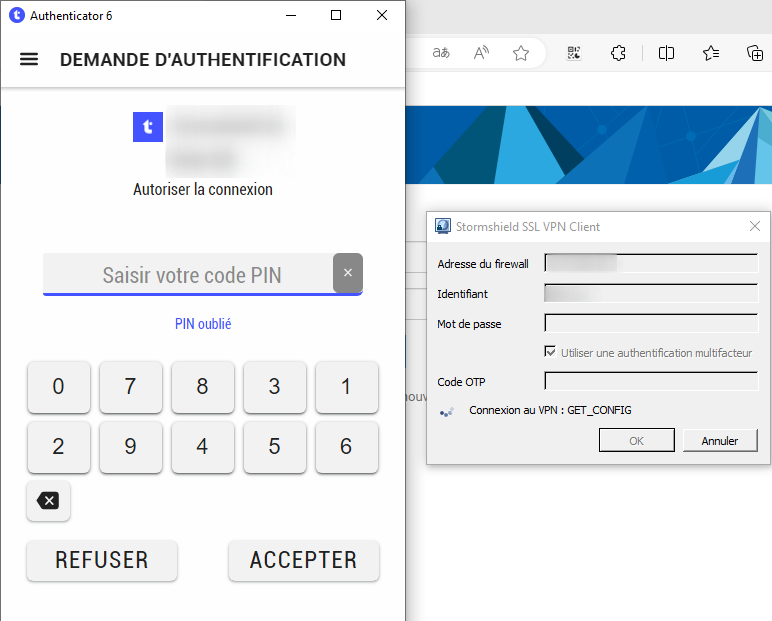
Test Authentication
Launch your Stormshield client (or SSL portail), enter your login and one random character into the password field then you can connect.
Your user will receive a notification on their TrustBuilder authenticator app (mobile or desktop).
Troubleshooting
Sometimes authentication via Radius may fail despite receiving an Access-Accept packet from the radius. The problem occurs during the first authentication attempt or after 30 minutes without any request to the radius.
The following xvpn log message will be found:
msg="Error during authentication : External authentication server did not reply"![]() This has been encountered for SNS appliances from 4.3.0 to 4.3.12 and SNS appliances from 4.4.0 to 4.5.4.
This has been encountered for SNS appliances from 4.3.0 to 4.3.12 and SNS appliances from 4.4.0 to 4.5.4.
To solve this problem we suggest a workaround (which has been tested on SNS version 4.5.3).
Connect via SSH and edit the
/usr/Firewall/ConfigFiles/Event/rulesfileAdd the following content:
CODE[ping_radius1] State=1 Start=* Period="5m" Exec="ping -c 1 -t 10 ip_radius1" #ip_radius1 must be replaced by the main radius object name [ping_radius2] State=1 Start=* Period="5m" Exec="ping -c 1 -t 10 ip_radius2" #ip_radius2 must be replaced by the backup radius object nameEnable both tasks by executing the following command:
CODEenevent
