Palo Alto networks (PAN-OS 8.0) SAML integration
Prerequisite
This guide has been documented for integration on Palo Alto PAN-OS® 8.0.
In this scenario inWebo will act as an Identity Provider.
Configuration
Configure an inWebo SAML 2.0 connector
In your inWebo service, in the "Secures Sites" tab, add a new SAML 2.0 connector.
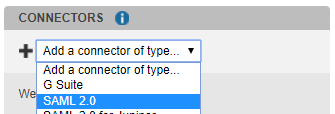
Name the connector and leave the other fields blank. Click "Add". This generates inWebo SAML metadata and certificate
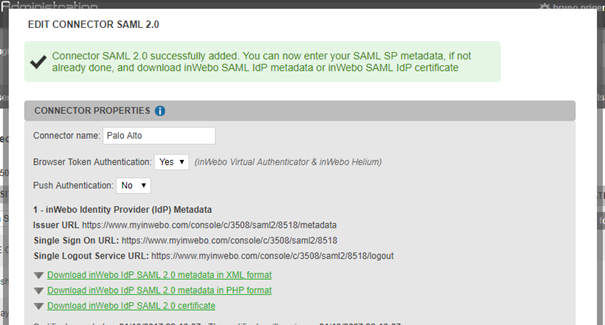
Download inWebo IdP SAML 2.0 metadata in XML format
Create a SAML Identity Provider
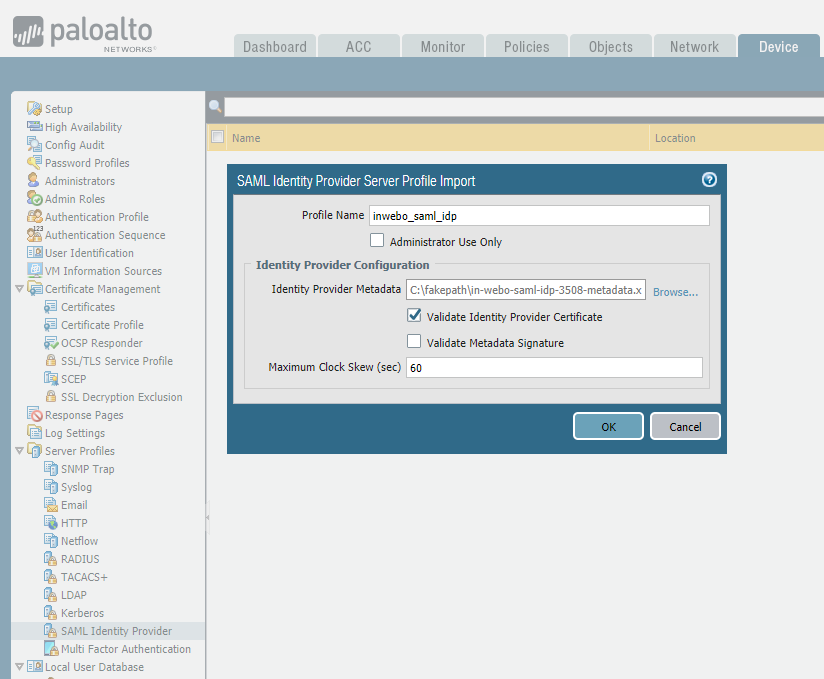
In the Palo Alto GUI select the "Device" tab and go to Server Profiles > SAML Identity Provider
Click on "Import" and locate the metadata file downloaded from inWebo. Make sure the file name meets the naming requirements from Palo Alto or you'll not be able to click on Ok
Create a Certificate Profile
The previous operation automaticaly imports the inWebo certificate. You can check the 2 entries exists in Certificate Management>Certificates
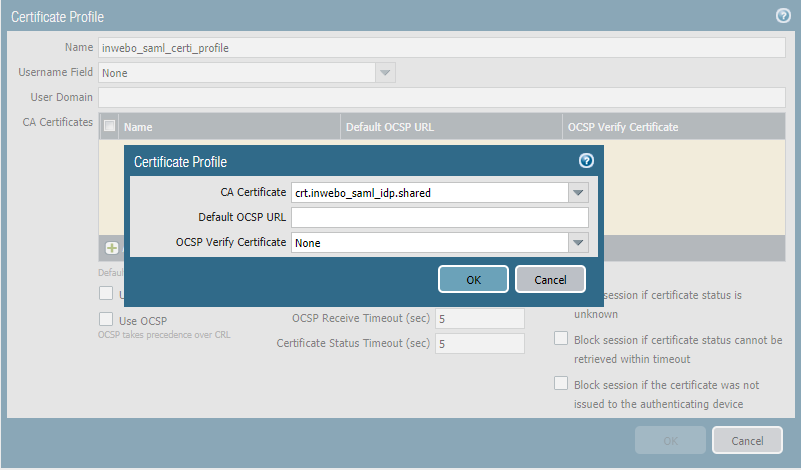
Go to Certificate Management>Certificate Profiles and click "Add". Name the certificate profile and Add the CA Certificate previously imported.
Configure an Authentication profile
Within the Device tab click on the Authentication Profile menu
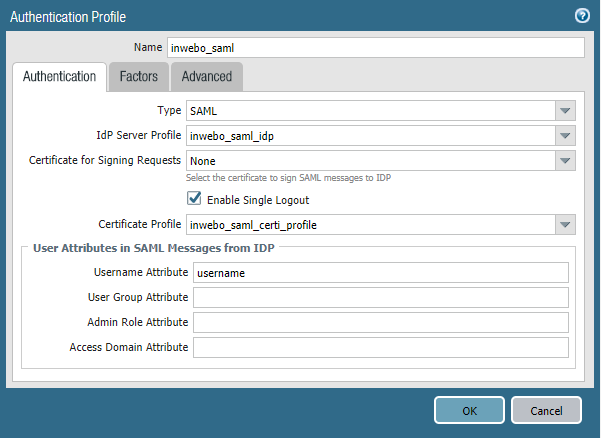
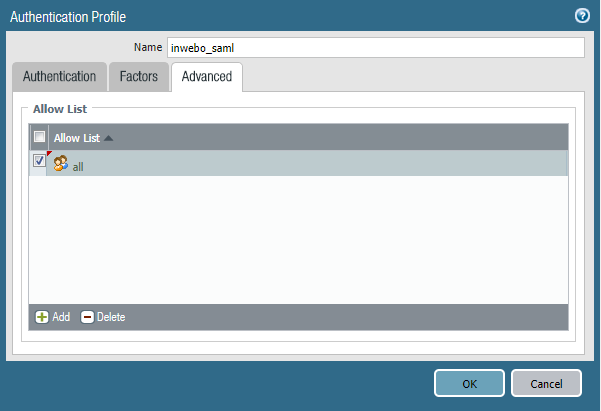
Click "Add", change the type to "SAML" then choose the Server Profile previously configured. Leave the "Factors" tab default configuration. In the "Advanced" tab make sure you allow your users to use this Authentication profile.
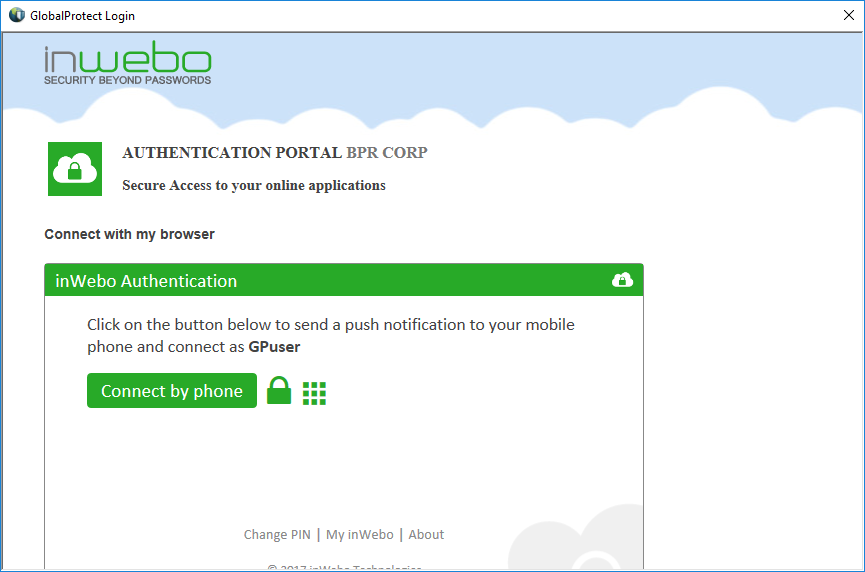
Use inWebo to authenticate your users
The user will connect using an OTP generated by an inWebo token or by receiving a push notification on his mobile.
Notice : if your firewall policies uses LDAP user groups you'll need to keep an LDAP authentication to retrieve the user group membership. inWebo doesn't know which LDAP user group your users are member of.
You may want to use MFA to control access to the GP Portal and/or the GP Gateway. If you choose to setup inWebo MFA for both Portal and Gateway then users will have to do MFA for both.
Typical setup enforce a login and password authentication on the GP Portal and inWebo MFA authentication on the GP Gateway.
Configure the Global Protect Portal to use inWebo MFA
Go on the Network tab and choose Global Protect > Portals menu
Add a Global Protect Portal configuration or edit an existing GlobalProtect Portal configuration
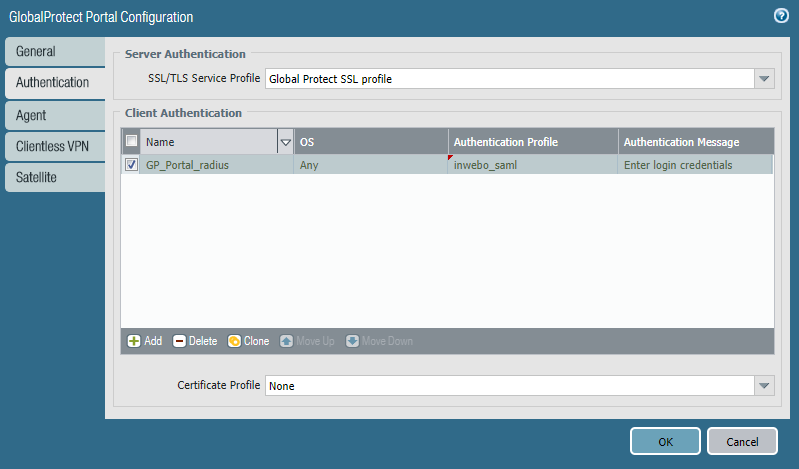
In the Authentication tab, declare a Client Authentication and choose the Authentication Profile you created
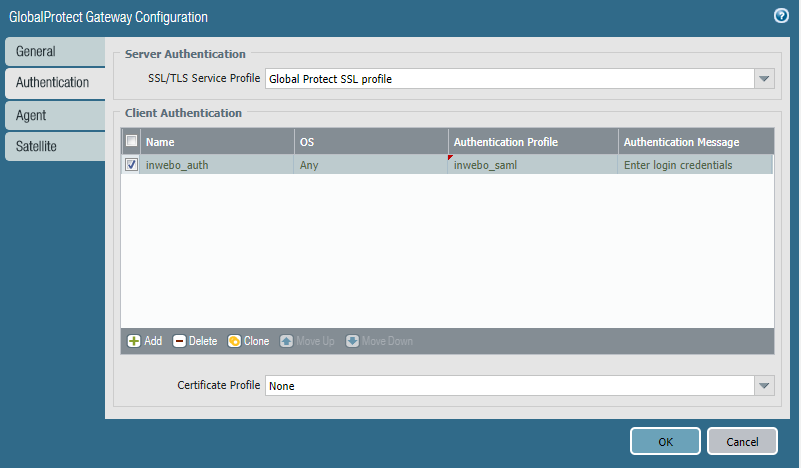
Configure the Global Protect Gateway to use inWebo MFA
The GP Gateway authenticates the user after the GP Agent succesfully authenticated the user against the GP Portal.
Go on the Network tab and choose Global Protect > Gateways menu
Add a Global Protect Gateway configuration or edit an existing GlobalProtect Gateway configuration
In the Authentication tab, declare a Client Authentication and choose the Authentication Profile you created
Commit
Configure inWebo
In the Palo Alto GUI go to Device tab and select the Authentication Profile menu.
Locate the SAML authentication profile created previously and Click on Metadata in the column Authentication
Choose the Service global-protect.
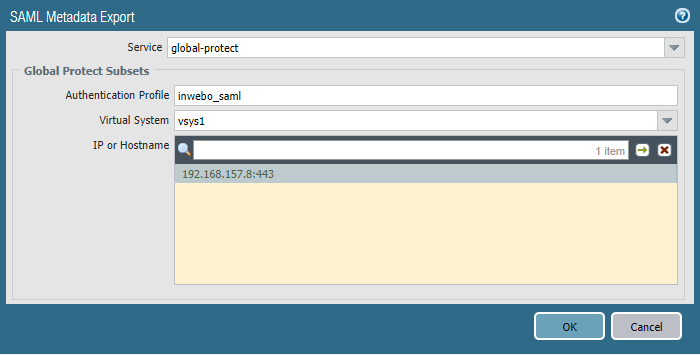
Notice : an extra Commit is sometimes required to make the IP/Hostname appear.
Go on the inWebo Administration Console and open the SAML connector created previously. Open the file generated by the Palo Alto gateway and copy/paste its content in the Section 2 of the SAML connector.
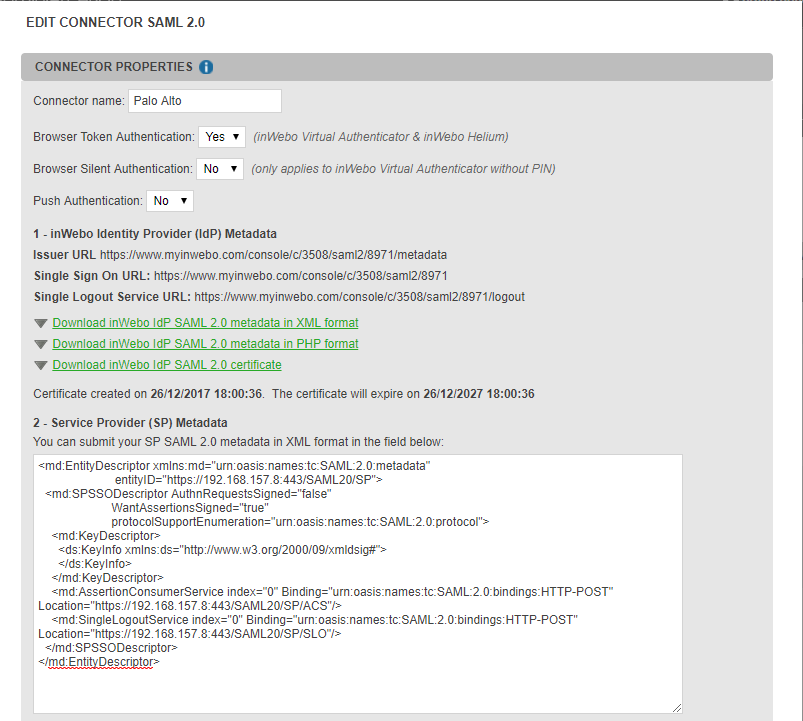
You can choose to customise the connector behaviour.
Allow Push Authentication
Allow SIlent Authentication (for service without PIN)
etc
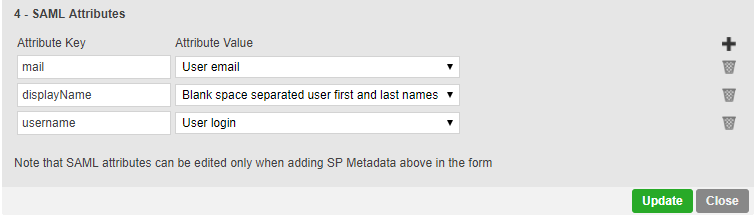
In Section 4 of the SAML connector add an extra attribute called "username" with the value "User login" and click on "Update"
Create a secure site
In your inWebo administration console, go to the Secure Sites tab.
Click on Add a secure site of type… and select the SAML connector name you previously configured.
Set the Called URL to point to your Palo Alto Internet address.
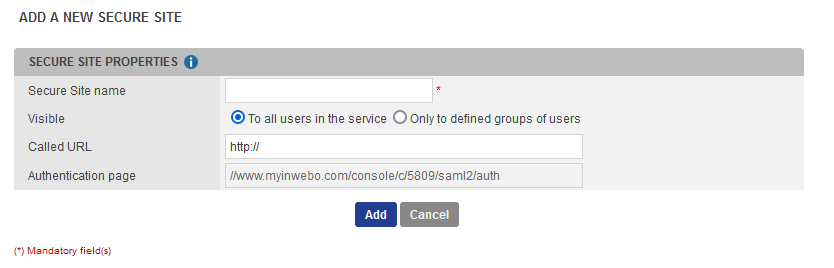
The Called URL setting is only used to set a bookmark for the user on their Myinwebo portal, it has no impact on the security.
Click on Add to create the secure site.
Extra configuration
If you want to adjust the user experience you may consider the following parameters
Browser Token Authentication
This parameter is available in the SAML connector configuration.
When set to Yes the user will be able to "enrol his GP Agent" and authenticate without mobile.
When set to No the user will be asked to enter his login so inWebo will send a push notification to his mobile.
Browser Silent Authentication
This parameter is available in the SAML connector configuration.
When set to Yes the inWebo Virtual Authenticator token will not need any user input. This requires to change the "Authentication mode" to "Without PIN" in your Service Parameter.
Since the PIN is not asked, you may want to add another authentication factor : you can change the Palo Alto authentication profile for the GP Portal or the GP Gateway to authenticate user with his LDAP credentials.
Push Authentication
This parameter is available in the SAML connector configuration.
When set to Yes the user will be able to connect via a Push notification on his mobile.