Evidian Authentication Manager
inWebo Radius connector configuration
You can create your own InWebo account at InWebo Signup page. This will give you access to the InWebo Administration Console.
- Once connected, go to Secure Sites tab > CONNECTORS section.
- Select “Add a connector of type…”, and choose “Radius” or “Radius Push” :
- The popup below will appear. Enter the public IP addresses of your EAM server, along with a Radius secret :
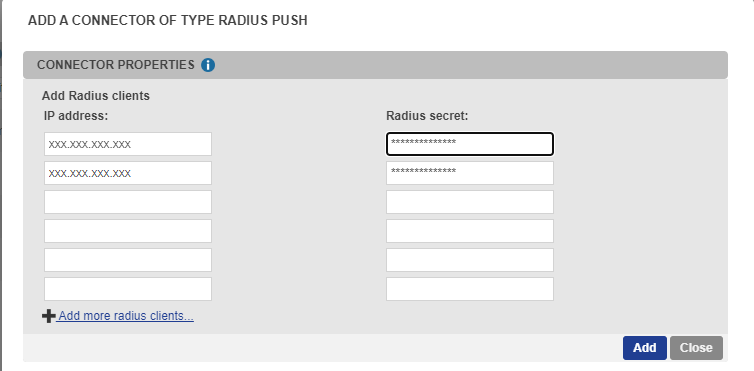
- Click “Add”.
Enterprise Access Management configuration
Declare inWebo radius server on Enterprise Access Management controller
inWebo Radius server addresses :
Primary: radius-a.myinwebo.com (95.131.139.137)
Secondary: radius-b.myinwebo.com (217.180.130.59)
(See https://inwebo.atlassian.net/wiki/spaces/DOCS/pages/2216886275/RADIUS+integration+and+redundancy for additional details and configuration)
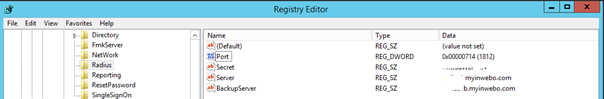
On Enterprise Access Management controller, add the following registry keys in HKEY_LOCAL_MACHINE\SOFTWARE\Enatel\WiseGuard\FrameWork\Radius
Key name 1: Server
Key type 1: REG_SZ
Key value 1: IP address or name of inWebo radius gateway (ex: radius-a.myinwebo.com)
Key name 2: BackupServer
Key type 2: REG_SZ
Key value 2: IP address or name of inWebo backup radius gateway (ex: radius-b.myinwebo.com)
Key name 3: Port
Key type 3: REG_DWORD
Key value 3: 1812
Key name 4: Secret
Key type 4: REG_SZ
Key value 4: The radius secret you previously configured in the inWebo Radius connector
Configure Enterprise Access Management controller
Open Enterprise Access Management console
Configure Access point profile
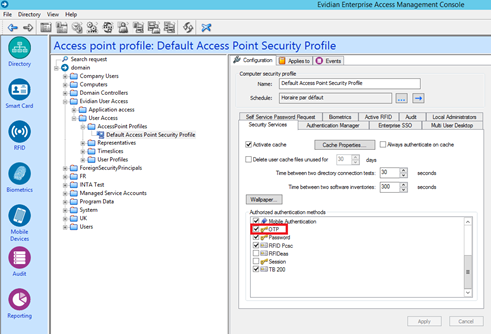
Configure User profile to allow OTP authentication
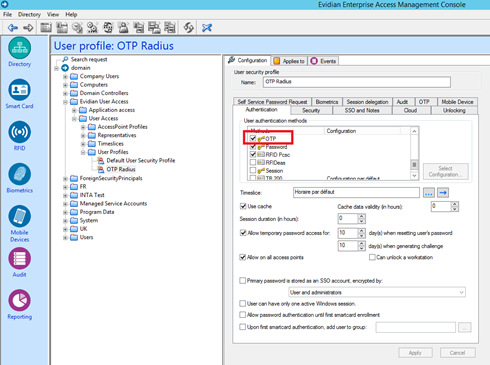
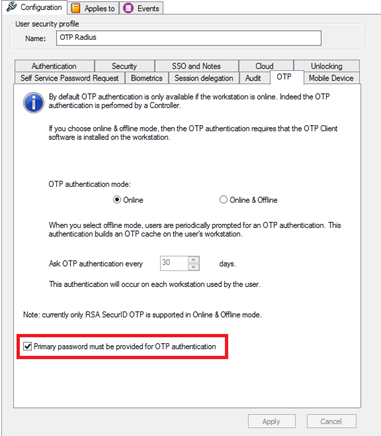
Optionnal : In order to authenticate users with login/password and an OTP, you have to configure the following option:
Enable inWebo for application SSO
Configure application profile related to applications to enable OTP authentication:
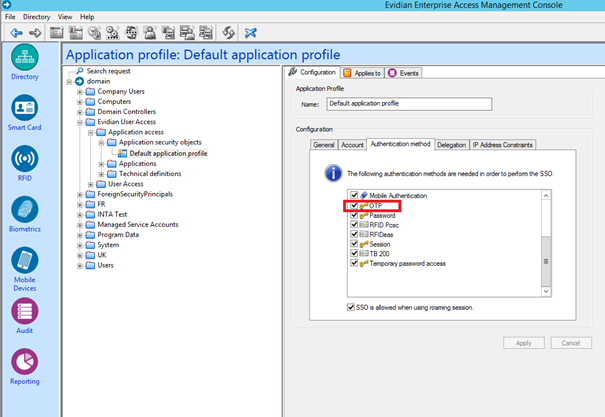
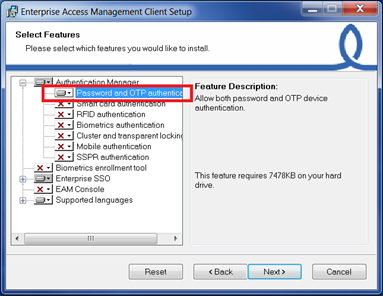
Configure Authentication Manager on the workstation
On the workstation, install Authentication Manager Module and select “Password and OTP authentication” feature: