Managing Certificates
About Certificates
The certificates overview shows all certificates available in the database.
There are two types of certificates:
Key Certificates : stored in the Key Store
Trust Certificates: stored in the Trust Store
Key Certificates vs Trust Certificates
Trust certificates can be used to establish a connection (TLS/SSL). They contain a trust chain that can be used to validate the certificate. They can also be used to encrypt a payload (using the public key). To import a Trust Certificate, your X509 file contains only the Public Key.
Key Certificates are certificates where the Private Key is also stored in our trust store, in addition to the a Certificate. They can also be used to establish trust, but have cryptographic uses beyond that (to decrypt payloads or to sign). To import a Key Certificate, your X509 file needs to include a Private Key. A Key Certificate can also be generated (ie. a Self-signed certificate).
Certificate Properties
Alias: Unique name given to the certificate by TrustBuilder, to identify the certificate in other sections of the application.
Serial Number: Used to uniquely identify the certificate within a CA's systems. In particular this is used to track revocation information.
Subject: The entity a certificate belongs to: a machine, an individual, or an organization.
Issuer: The entity that verified the information and signed the certificate.
Not Before: The earliest time and date on which the certificate is valid. Usually set to a few hours or days prior to the moment the certificate was issued, to avoid clock skew problems.
Not After: The time and date past which the certificate is no longer valid.
Key Usage: The valid cryptographic uses of the certificate's public key. Common values include digital signature validation, key encipherment, and certificate signing. However, this usage property is not obeyed necessarily by TrustBuilder.
Extended Key Usage: The applications in which the certificate may be used. Common values include TLS server authentication, email protection, and code signing.
Public Key: A public key belonging to the certificate subject.
Signature Algorithm: The algorithm used to sign the public key certificate.
Signature: A signature of the certificate body by the issuer's private key.
Creating or Importing Certificates
You can choose to create your own certificates (self-signed, or to be signed by a Certificate Authority); or you can choose to import existing certificates or keystores into the TrustBuilder keystore.
Generate Key Certificate
Field | Description |
|---|---|
Alias | The name by which the certificate is referenced. |
Algorithm | Defines what kind of Key Pair algorithm is used. |
Validity | How long the certificate will be valid (In Months) |
Subject | The subject definition of the certificate. Contains the certificate's identifying information. |
Extension Parameters | The Key Usage extensions define what a particular certificate may be used for, as described in https://tools.ietf.org/html/rfc5280#section-4.2 |
Certificate Signing Request
Once a certificate is created, it is considered self-signed. To get a signed certificate, export the "Certificate Signing Request (CSR), and submit it to your Certificate Authority (CA). Once the certificate is returned, signed by the CA, it can be imported, and this import will replace the self-signed certificate.
The advantage of this method, is that the private key is never exposed, as it is not included when submitting it to the CA.
Importing a Certificate
Any standard type of certificate can be imported. As long as it is a singular certificate. To import multiple certificates, use the "Import Keystore" function.
If a certificate is imported, which contains a private key, it is strongly recommended to encrypt the certificate using a password.
Field | Description |
|---|---|
Alias | The name by which the certificate is referenced. |
Contains Private Key | Whether or not the certificate contains a private key. |
Password | The key with which the certificate's private key is encrypted. |
Importing Keystore
This function allows you to import a keystore (PKCS12 files) ; however it is not possible to import a java keystore (jks). A keystore contains one or more certificates, which are protected (encrypted) with a password.
Using Certificates
Adding certificates
Certificates can be used for the following entities:
Service Provider
Type SAML2
Type OAuth Client
WS Federation
Identity Provider
Type SAML2
Type OAuth 2.0
When Adding certificates, you need to specify the context, the alias and the usage period.
Below is a matrix which certificate types and contexts are available for each type of SP and IDP
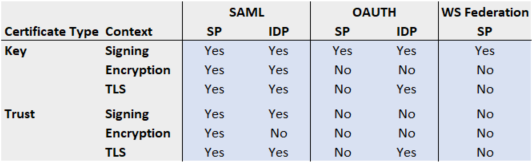
Context
SAML:
Contexts on Service Provider
Key Signing: Certificate used to sign the Authentication Request to the IDP
Trust Signing Certificate used to validate the signature of the Assertion Request
Key Encryption: Certificate used to decrypt the Authentication Request
Trust Encryption: Certificate used to encrypt the Assertion Request
Key TLS: Server Certificate used for the Service Provider to establish a secure connection using TLS for Artifact Resolution.
Contexts on Identity Provider
Trust Signing: Certificate used to validate the signature of the Authentication Request
Key Signing: Certificate used to sign the Assertion Request to the IDP
Key Encryption: Certificate used to decrypt the Assertion Request
Trust TLS: Client Certificate used to establish a connection using TLS to the IDP for Artifact Resolution
OAUTH:
Contexts on Service Provider
Key Signing: Certificate used to sign the JWT Tokens
Contexts on Identity Provider
Key Signing: Certificate used to sign the JWT Tokens in case of Client Authentication
Trust TLS: Certificate used to establish a connection using TLS to the IDP
WS Federation:
Signing: Certificate used to sign the Authentication Request
Certificate Alias
Select the certificate for this context.
Note: Expired Certificates cannot be selected here.
Usage period
Can be used to further specify the time boundaries on certification usage.
For example when renewing an encryption certificate, there can be no overlap period. So adjusting these setting allows you to seamlessly move from one certificate to another.
The default values are copied from the Certificate validity period.
