AZN Policies in TrustBuilder Administrator
The TrustBuilder administration tool allows the user to edit resources and rule suites by selecting the Policies tab.

Prerequisites
The login user must have the TBAGPolicies role.
Editing policies
Clicking the policies tab allows the user to enable / disable the authorization engine, and to define resources and rule suites.

Enabling / disabling the authorization engine
The top-right check box enables / disables the authorization engine. This action updates the authorization service section in the TrustBuilder configuration file.
Managing resources
The Resources tab of the policies page allows the user to manage the list of resources. Resources may be created, edited and removed. Only resources linked to a rule suite will be taken into account by the authorization engine.
When creating a resource, a properties pane appears on the right. Clicking Save creates the new resource. Clicking the Edit button of a resource opens the properties pane again.

Adding rule suites
The Rule Suites tab allows administrators to add, edit and remove rule suites.
When creating a rule suite, a properties pane appears on the right. Clicking Save creates the new rule suite. Clicking the Edit button of the new rule suite opens the properties pane again.

The new rule suite can now be linked to the appropriate resource(s) on the resources tab.
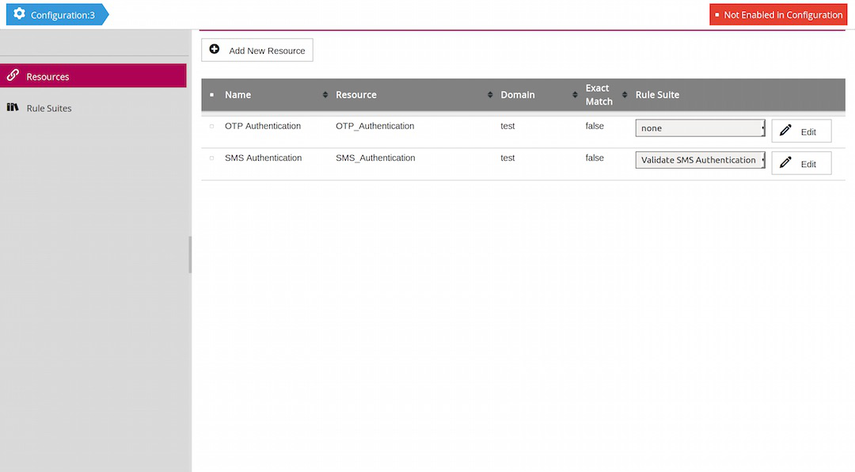
Clicking the rule suite's Rule button opens a page where the user can add rules and Policy Information Points.
Adding Policy Information Points to a rule suite
The Policy Information Point (aka PIP) tab allows the user to retrieve external information based on the input of the rule suite and store this information in a variable.
When creating a PIP (or editing an existing PIP), a properties pane appears on the right. This pane allows the user to name the variable and set the input data for the PIP request. The input data are entered as a list of key-value pairs and converted into a simple JSON-like document.

Once the PIP is defined, the user can specify the TrustBuilder workflow that must execute the request.
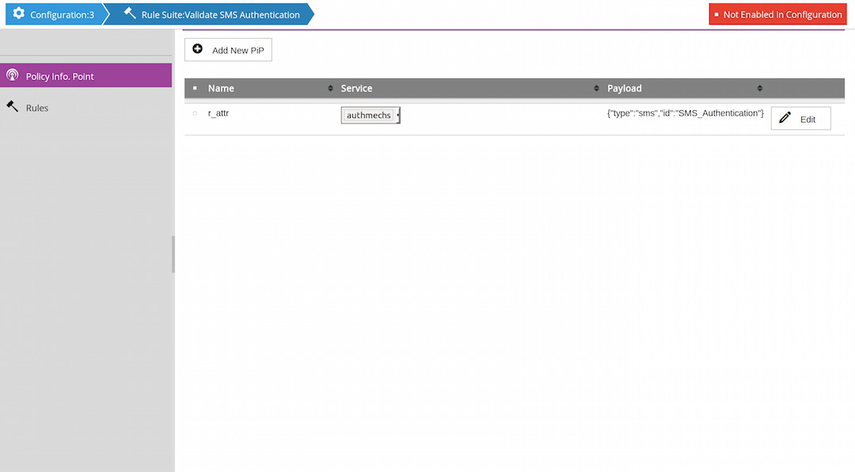
The Payload column on this page shows the generated JSON document.

Adding rules to a rule suite
The Rules tab allows the user to manage the rules in the selected rule suite.
When creating a rule (or editing an existing rule), a properties pane appears on the right. This pane allows the user to name the rule, and, optionally, to specify a name for the variable memoizing the result of the rule execution.

The Define button allows the user to specify the rule conditions, assertions and hints.

Note
As in other screens of the administration tool, the tabular view of the rule list uses a filter to constrain (per column) the elements to be displayed (the input fields below the table header). If this filter is 'on' when a new rule is created or when an existing rule is edited, the saved rule may not show up in the list if it does not satisfy all the constraints of the filter.
Conditions
The Conditions tab allows the user to specify an optional condition for the rule execution. This consists of one or more tests (basic conditions), using one of the following logical combinations:
AND
OR
NOT AND
NOT OR.
Each test consists of a function applied to one or more parameters. The functions are grouped by category (string functions, number functions, ...).
To add a test, the user selects a function from the list on the right. The user interface adjusts the number of input fields according to the parameters of the function. For readability, the first parameter is placed to the left of the function.
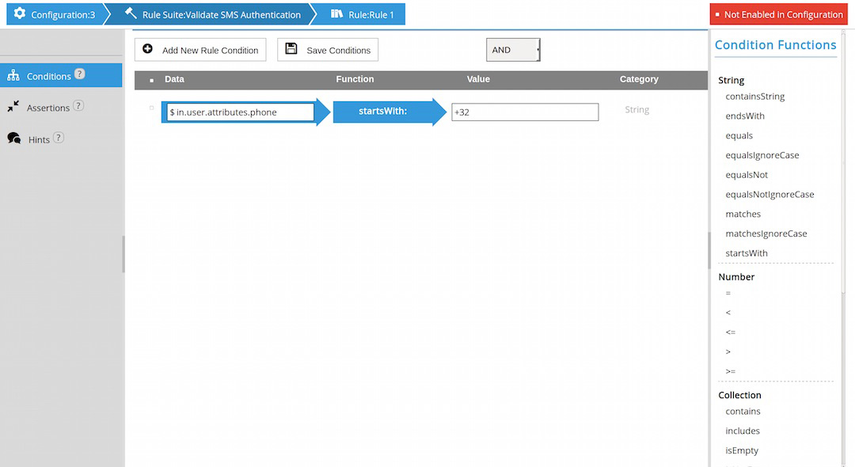
Note Only tests with valid parameters (non-empty after trim) are retained (e.g. after save).
Assertions
The Assertions tab allows the user to specify the assertions for the rule. This consists of one or more tests (basic assertions), using one of the following logical combinations:
AND
OR
NOT AND
NOT OR.

The assertions editor works in a similar way as the conditions editor.
Hints
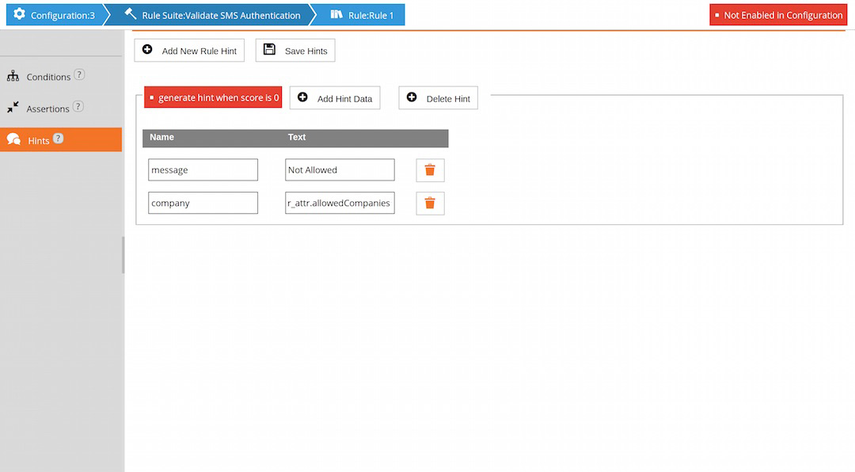
The Hints tab allows the user to optionally specify one or more hints. Each hint consists of a simple JSON-like document and is constructed similarly to the PIP input data, i.e. by means of a list of key-value pairs.
By default, a hint is only generated when the rule fails (score 0). When the Always Generate Hint option is set, the hint will also be generated if the rule is executed, but does not fail.
Values in condition and assertion input fields
Values in input fields are converted into internal data types according to the following scheme:
Try to interpret the value as a boolean (true or false).
If the value is a double quoted string, then the value is the string between quotes. Thus "abc" becomes abc, "$a.b.c" becomes the string $a.b.c and ""abc"" becomes "abc".
Try to interpret the value as a number.
Try to interpret the value as a document.
Try to interpret the value as a sequence.
Try to interpret the value as a variable (accessor).
Use the value as is (a string).
Values in PIP and hint data
The input fields in PIP and hint data are converted into keys and values of JSON objects using the standard JSON parser. Thus value "123" becomes the number 123, while "abc" remains the string abc. The administration tool also stores variable references as strings within the JSON object. When the authorization engine parses that JSON data, it tries to interpret a value of the form "$A.x.y" as a variable.
